Practical Linux Forensics by Bruce Nikkel, a professor of applied sciences at Bern University in Switzerland, (No Starch Press) covers how to search a Linux-based system for digital evidence that will allow you to draw conclusions and create forensic reports about a particular case or incident. The book is thorough, spanning 398 pages. It covers the specifics of the examination process including identifying various aspects of hard-drive contents, searching for specific content, extracting evidence traces, interpreting information, and reconstructing past events.
The book starts with a general overview of digital forensics with special emphasis on producing digital evidence that can be used in  a court of law. The book also provides an introduction to modern Linux systems and even includes tips on analyzing the Linux-based Raspberry Pi computer. Also covered are traditional antiforensic techniques involve encrypting data on a drive or employing steganography to hide evidence and efforts around antiforensic countermeasures such as a means to detect the manipulation of logs.
a court of law. The book also provides an introduction to modern Linux systems and even includes tips on analyzing the Linux-based Raspberry Pi computer. Also covered are traditional antiforensic techniques involve encrypting data on a drive or employing steganography to hide evidence and efforts around antiforensic countermeasures such as a means to detect the manipulation of logs.
Nikkel organized his book around nine areas where investigators might logically look for signs of mischief: storage devices, directories, logs, system boot and initialization, installed software, network configuration artifacts, time and location shenanigans, desktops and login, and attached devices. Most of the storage discussion covers hard drives; his message about SSDs is that investigators are usually out of luck trying to get much out of them without physically unsoldering the ICs. “We are coming to the end of a ‘golden age’ in filesystem forensics….today SSDs are accepting TRIM and DISCARD commands from the operating system that instruct the SSD firmware to erase unused blocks (for performance and efficiency reasons)….Because of this, some traditional forensic techniques are becoming less effective at recovering data,” Nikkel relates.
Nevertheless, there are plenty of other areas in a Linux system that can reveal secrets. Among them are the early boot stages where the BIOS or UEFI firmware pass control to the bootloader, the loading and executing of the kernel, and systemd initialization of a running system. Nikkel also includes an analysis of power management activities like sleep and hibernation, and the final shutdown process of the system, though he cautions that the analysis of maliciously modified bootloaders is a complex subject, so he covers only the extraction of bootloader components and the data to be analyzed.
In the current environment where it doesn’t pay to trust software packages coming in from the outside, one of the more interesting sections covers the package management systems for software already installed (or previously installed) on a machine. This includes analysis of the repositories from where packages were downloaded, where the package contents were placed on the filesystem, databases to track the installed packages, installation logs, and more. Readers are instructed on how to identify the installed software distro and version numbers, and reconstruct the initial installation process. Covered as well is how to determine which additional software packages are installed and how to analyze the details of those packages.
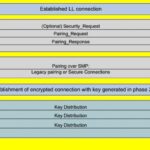
Given the wide use of Linux systems in IoT applications, the book’s coverage of networking configuration and reconstruction of past network activity is potentially quite useful. Nikkel describes common Linux network configurations for both static systems like servers and dynamic clients like desktops and roaming laptops. The analysis includes network interfaces, assigned IP addresses, wireless networks, attached Bluetooth devices, and more. Security coverage includes examining evidence of VPNs, firewalls, and proxy settings, WiFi, and WWAN mobile technology. Each of these technologies leave traces of evidence on the local system that may be of interest to forensic investigators. Nikkel also covers how to identify WiFi artifacts and paired Bluetooth devices and analyze WWAN mobile activity. In addition, he explores Linux network security such as VPNs, firewalls, and proxies.
Nikkel says he wrote the book for computer forensic analysts who have worked on Windows and Mac systems and who now want to undertake similar investigations on Linux machines. But even if this is your first foray into computer forensics, there is a lot to be gained from Nikkel’s book.




Leave a Reply