State-of-the-art countermeasures help make IoT products bullet-proof to ever-improving power analysis attacks.
Marius Munder • Silicon Labs
There’s a growing focus on security among manufacturers of IoT products, driven in part by how high-profile attacks affect buyer behavior. When an attack or data breach makes headlines, regardless of its actual severity, consumer confidence erodes, and vendors face reputational damage. Manufacturers know that buyers understand the potential consequences of poorly designed smart locks or alarm systems. Establishing a reputation for trustworthiness is, therefore, top-of-mind for vendors.
The weapon of choice for a wide range of attacks is differential power analysis (DPA). This technique uses statistical analysis on a device’s power consumption as a side-channel to extract keying material or other secrets. There are several ways attacks can utilize DPA, but all of them have one thing in common: They require incredibly complex equipment and algorithms. Nevertheless, sufficiently sophisticated criminal hackers can employ these attacks, so they are moving outside the lab and into the real world.
More specifically, DPA requires that the attacker understand what kind of computer operations take place during security procedures such as DES (Data Encryption Standard) encoding. DPA attacks measure power levels at different parts of the chip and apply statistical analysis to overcome countermeasures, such as added noise, applied to obscure the power signature of individual bits. Measurements of power use identify the computational operations the device executes. Analysis will reveal several of the cryptokey bits at a time. Repeating the process eventually produces the entire key.
For example, the original paper that introduced DPA included the following discussion: The DES key schedule computation involves rotating 28-bit key registers. A conditional branch is commonly used to check the bit shifted to the end so that “1” bits can be wrapped around. The resulting power consumption for a “1” bit and a “0” bit will contain different features if the execution paths take different branches for each. Similarly, DES implementations perform a variety of bit permutations. Conditional branching in software or microcode can cause significant power consumption differences for “0” and “1” bits. And string or memory comparison operations typically perform a conditional branch when a mismatch is found. This conditional branching causes large power (and sometimes timing) signatures.
In 2015, a project called ChipWhisperer was funded through a Kickstarter campaign. Its success put power analysis into the hands of white-hat hackers as well as hobbyists. Besides power analysis, ChipWhisperer focuses on voltage and clock glitching attacks, which briefly disrupt a device’s power or clock to cause unintended behavior (such as skipping a password check). ChipWhisperer includes open-source scope boards used to mount side channel attacks, firmware for both scopes and targets, and an open-source Python library for controlling the capture hardware and communicating with the target.
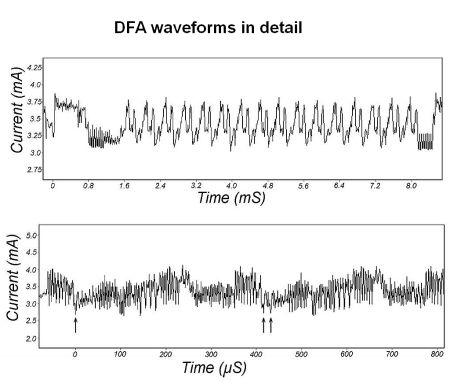
The ChipWisperer tool (amongst others) drove IoT manufacturers to add countermeasures. Utilizing this open-source toolchain, Silicon Labs set out to prove that the hardware-based countermeasures in its new chipsets were indeed preventing the leakage of confidential data. The tests involved the extraction of a 128-bit advanced encryption standard (AES) key and the impact of the correct choice of physical extraction method for the traces. (Here, a trace refers to a set of power consumption measurements taken across a cryptographic operation.
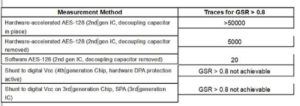
For example, a 1-msec operation sampled at 5 MHz yields a trace containing 5,000 points.) Importantly, the results show that it only takes a relatively small number of traces to learn the cryptokeys of legacy hardware, which may remain in service for years beyond the effectiveness of its security features.
The same measurement was repeated using a fourth-generation wireless SoC with hardware DPA protection built in. Measurements were run as well on a third-generation IC with no DPA protection. Here the attack method was a simple power analysis (SPA) where data is simply extracted by monitoring a power trace and decoding tiny fluctuations on the supply lines into “0s” and “1s” of extracted data. In these two scenarios, the protection offered an effective defense.
Preventing information leakage
The simplest way to protect information is to make physical extraction more complicated. Encapsulating the hardware at the board level boosts the cost and complexity of attacks. But encapsulation may increase the cost of the device disproportionately. When moving from board to chip level, there are several relevant countermeasures:
First, state-of-the-art CMOS technology nodes require significantly less power, greatly reducing the amount of information accessible through power analysis. Second, power analysis becomes much more difficult when using fast crypto engines with a high level of parallelization. The reason is the parallelization creates a significant amount of background noise. Then extraction of any keying material requires more traces and/or more advanced attack methods to separate the signal from the noise. Finally, it’s possible to randomize the emissions from a chip in a way that makes it impossible to extract any data using power analysis.
The key to devising software that thwarts power analysis attacks is to keep in mind the state of secret data should not lead to a specific power or timing pattern. This goal can be achieved if the execution path does not depend on secret values but instead only uses publicly known data for branch code execution. In situations where this branching is isn’t possible, all potential execution paths should require the same number of execution cycles.
These relatively simple and inexpensive software-based countermeasures can help make SPA impossible. However, when it comes to DPA and more complex methods of power analysis, this strategy mostly just increases the number of traces needed to extract secret data because each operation in a modern processor has a distinct power fingerprint. It’s virtually impossible to make the power profile entirely data- and execution-independent using just software countermeasures.
For any side-channel attack to succeed, the device-under-attack must use the secret an attacker is trying to extract in a way that is traceable. So, the most obvious and potentially most powerful countermeasure is to rate-limit the number of times a usable trace can be recorded. For example, assume an IoT device uses elliptic curve cryptography (ECC) to derive a communication key when it joins a new network. For a legitimate user, there is no “use case” involving attempts to join the same network repeatedly at a high rate. So it may be acceptable to restrict join attempts to just once per minute.
All in all, DPA is available to a broad range of attackers, including hobbyists. It takes minimal time and effort to extract keying data from a legacy wireless SoC. The addition of state-of-the-art countermeasures will help make products more resilient to ever-improving power analysis attacks for many years.




Leave a Reply