Resilient GPS/GNSS receivers protect inertial navigation systems from jamming and spoofing.
Maria Simsky, Septentrio
The demand for accurate and affordable navigation is on the rise thanks to the growth of automation and robotization. Of course, the go-to technology for navigation is GPS—able to locate receiver position to within 16 ft or less—and other GNSSs: Russia’s Global Navigation Satellite System (Glonass), China’s BeiDou Navigation Satellite System, the European Union’s Galileo, Japan’s QZSS and India’s NavIC.
Most autonomous navigation technologies include an inertial navigation system (INS), which consists of a GNSS receiver and an inertial measurement unit (IMU) sensor. The GNSS receiver provides absolute positioning in terms of geographic global coordinates while the IMU measures heading, pitch and roll angles which give orientation information about the system on the move.
While GNSS provides absolute positioning, the IMU measures relative movement, which is subject to cumulative error called drift and needs regular “recalibration.” In a GNSS/INS system both sensors are fused in such a way that the GNSS provides regular IMU “calibration” and the IMU provides angles and extrapolation or “smoothing” of GNSS.
When selecting a GPS/GNSS positioning receiver it is crucial to understand the vulnerabilities of its sensors and how vulnerabilities could affect the navigation system. For robots and autonomous devices, availability is key to ensuring continuous and reliable service. Safety also must be considered for robots and drones operating near people. GNSS jamming or spoofing must be detected and flagged immediately so other sensors can take over.
Jamming overpowers weak GNSS signals, causing accuracy degradation and possibly even loss of positioning. In a nutshell, jamming arises when a signal at the GNSS frequency is strong enough to overwhelm the GNSS receiver, preventing it from seeing the real GNSS satellite signal (which is typically on the order of -125 dBm). Unintentional jamming sources include radio amateurs, maritime and aeronautical radiolocation systems as well as electronic devices sitting close to the GNSS receiver. There are also intentional jamming devices; these “jammers” are sometimes found on vehicles trying to avoid road tolls.
Jamming results in loss of positioning so the GNSS receiver can no longer be used as part of the INS solution. Jamming can lead to longer INS initialization times or a switch to dead-reckoning mode (IMU only), where position accuracy starts to drift. Jamming can also result in measurement outliers which impact both deep and tight-coupling GNSS/INS algorithms. (Briefly: In loosely-coupled algorithms, the positions and velocities estimated by the GPS receiver are blended with the INS navigation data. In the tightly-coupled method, GPS raw measurements are processed through a unique Kalman filter with the measurements coming from the inertial sensors to estimate the position, velocity, and time. The main advantage of the tight integration is the possibility to update the position in scenarios with poor signal quality or limited coverage.)
Spoofing is a real threat to GNSS-based INS systems. It is mitigated most effectively by incorporating security mechanisms into all system sub-components. However, because spoofing takes place on the level of the GNSS signal, the receiver can employ a number of sophisticated methods to detect and mitigate spoofing.
Basically, spoofing is an intelligent form of interference which makes the receiver believe it is at a false location. During a spoofing attack a radio transmitter located nearby sends fake GPS signals into the target receiver. In one spectacular spoofing experiment a Tesla car was “misled” to take an exit from a highway rather than following the highway as it was supposed to. Another example arose when Pokémon GO fans used inexpensive software-defined radios to spoof their GPS position and catch the elusive Pokémon without leaving their home.
There are two principal ways of spoofing. The first is dubbed meaconing. It consists of intercepting, storing, and then rebroadcasting GNSS signals later on. The second consists of generating and transmitting modified satellite signals.
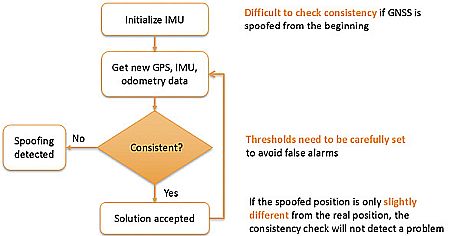
During a spoofing attack an INS could be “hijacked” if the spoofer uses small increments in positioning, which common anti-spoofing methods may not detect. For example, GNSS/INS systems can have a drift of a meter or more when GNSS satellite transmissions are lost for longer periods. Spoofers can exploit this drift phenomenon to hijack positioning gradually, in increments comparable to the expected drift.
To combat spoofing, GNSS receivers must decipher spoofed signals from authentic signals. One telltale sign: Spoofed signals are often a lot stronger than ordinary satellite signals, so a large signal is suspicious. Once signals are flagged as spoofed, they can be excluded from positioning calculations.
Use of sensors other than GNSS, such as an IMU or odometry, can help flag spoofing by detecting inconsistencies between GNSS and the other sensors. While such sensors help reduce spoofing risks, they are insufficient to provide full protection because they only output relative positioning which also is subject to drift.
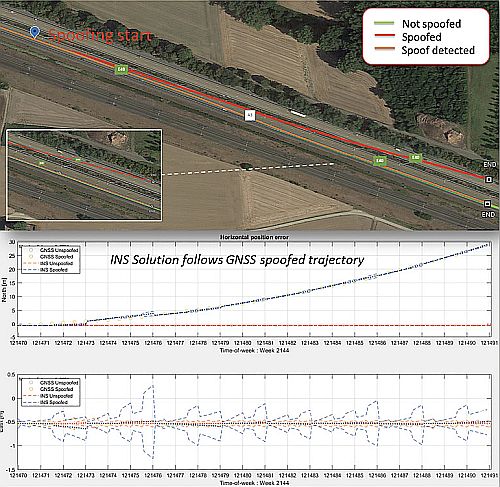
A common technique used by GNSS/INS systems to detect spoofing is to continuously check GNSS, IMU and odometry data for consistency. If the spoofing attack keeps positioning increments within the allowed thresholds, which are set to allow for drift, it would go undetected by such a mechanism. That is why anti-spoofing resilience should be built into several system components on both GNSS and INS levels.
Detecting spoofing
When anti-spoofing is built into the GNSS receiver, the system rejects the spoofed signal and switches to dead-reckoning, which allows it to stay on the right track. If the spoofing attack is limited to a few signals, the GNSS receiver can avoid the attack by discarding these spoofed signals from its positioning calculations.
An INS system will be more resilient if the GNSS receiver can indicate spoofing or, even better, if it can mitigate spoofing itself. Thus, it is important to understand what constitutes a strong internal anti-spoofing defense system or a warning system. One aspect of anti-spoofing is to provide lots of information about received GNSS signals, giving users insights into spoofed signals such as time stamps and power levels.
A GNSS receiver design which implements security measures will include spoofing resilience at various levels. For example, consider the Septentrio AIM+ Advanced Interference Mitigation technology. It is a jigsaw puzzle of various anti-jamming and anti-spoofing components built into receiver hardware as well as software:
• Signal processing hardware includes OSNMA (Open Service Navigation Message Authentication), a data authentication function. Galileo is the first satellite system to use OSNMA anti-spoofing directly on its signal. This feature provides assurance that received Galileo navigation messages are authentic and have not been modified. Other security measures include signal comparison and anomaly detection, and satellite consistency check-in tracking—basically looking at signals from multiple satellites for consistency.
• Measurement engine (software): quality checks of raw measurements
• Positioning engine (software): receiver autonomous integrity monitoring (RAIM+) and proprietary algorithms. RAIM+ cross-checks for individual measurements that disagree from the rest sufficiently to create a potential for unaccepted errors. It requires measurements from a minimum of five satellites to detect a faulty measurement and at least six satellites to detect and exclude a faulty measurement.
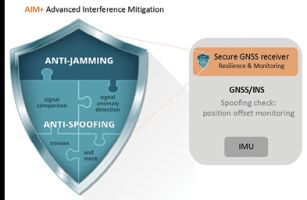
Both the GNSS receiver as well as the INS have their own mechanisms for spoofing protection. But resilience comes from the combination of detection and mitigation mechanisms working together on component level.
As in any field affiliated with security, continuous improvement is a necessity for anti-spoofing and anti-jamming mechanisms. The concepts discussed in this article are valid not only for GNSS/INS systems but for any sensor fusion system, which includes a GNSS receiver. Smart GNSS technology protects receivers from jamming and spoofing at the core level, ensuring safe and reliable system operation.
References
Tesla Model 3 spoofed off the highway – Regulus navigation system hack causes car to turn on its own