When you’re done with a data storage drive, it’s nice to make sure that all of the data is scrubbed from it. A drive that’s returned, repurposed, or discarded can have personal or confidential data on it. Discarded drives have been found with everything from financial and medical data, email, and even pornography on them. New personal computers are migrating from standard Hard Disk Drives (HDDs) to Solid State Drives (SSDs). SSDs are generally faster to access if they are not too large. (Addressing can get cumbersome and start to get slow if you start to have addresses greater than 32-bits long). However, permanently erasing SSDs is not the same as for HDDs. HDDs can be overwritten multiple times, which takes some time to do. However, for most SSDs no overwrite command is available for sanitizing the drive. Methods to sanitize HDDs often do not work on SSDs. Erasure methods are very different between the two storage technologies. The term “sanitize” describes a process where data is irretrievably removed from a storage device such that it is not possible to forensically (or otherwise) reconstruct it.
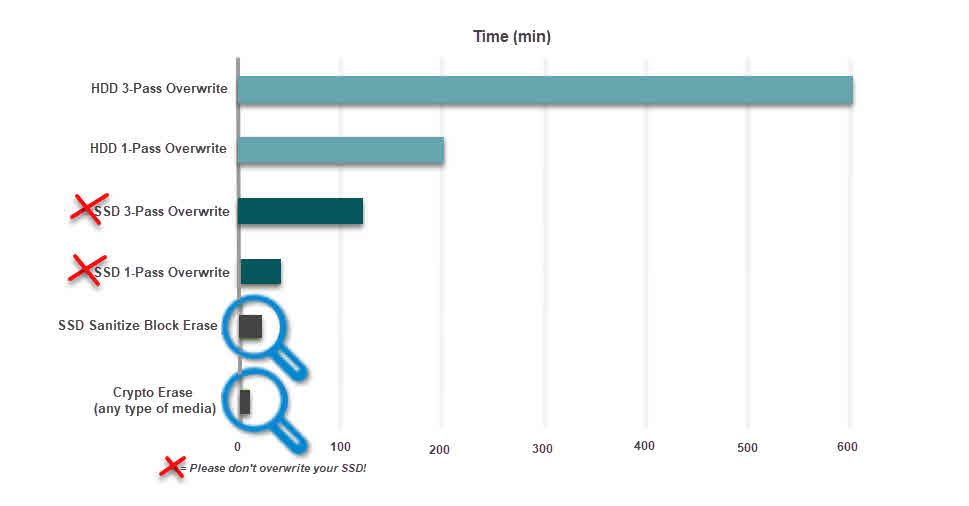
There are a few methods for permanently destroying data on a drive: A Crypto Erase applies to self-encrypting drives that allow you to change the media encryption key. Once the encryption key is changed, the data becomes inaccessible or no longer understandable. Another well-known sanitization operation is to overwrite the existing data with something else. Overwriting data doesn’t work well with SSDs because SSDs don’t work like traditional HDDs. One of the reasons it’s a problem to overwrite NAND flash SSDs is that the system has to issue an ERASE command first before it can perform a WRITE command to the same physical location.
Another way to sanitize NAND flash-based SSD is by using Block Erase on every element in the flash array. Block Erase sets the voltage level on each storage element to a significantly higher level than the standard operating voltage and then drops it to ground. Another method to sanitize a drive is to physically destroy the hard drive platter with a hammer or destroy the silicon chip of the SSD by shredding it or otherwise physically destroying it. (Note: shredding the silicon might damage your shredder machine.) The latter method is final, however, in that the drive is permanently destroyed and cannot be re-used as if fresh out of the box as can be done with other methods. Secure erase will delete the mapping table for the drive but will not wipe all of the blocks that have been written on. Sanitization not only removes the map but also erases all blocks that have been written on. If you have an NVMe SSD, the NVMe specification supports a sanitize command. NVMe, ATA, and SCSI sanitize commands were designed to erase SSD storage that’s accessible via both the host interface and the internal firmware of the drive.
Secure erase is faster, but not as complete. Data on a drive that has been securely erased or sanitized cannot be recovered. If power is interrupted during a secure erase, secure erase may continue as soon as power is restored or the user may need to issue another secure erase command when power is restored. Note that SSD manufacturers do not follow a universal command to sanitize drives.
Erasing an SSD with a Sanitize Block Erase (e.g., on Micron SSDs) can be much faster than using overwrite command on an HDD. On an HDD, a bit-by-bit overwrite operation can take hundreds of minutes since two to three passes are recommended. But on a Micron SSD, for example, the Block Erase command can be implemented on many blocks simultaneously so that a 1TB drive can be sanitized in about one minute (Figure 1). If possible, use the software provided by your SSD manufacturer to sanitize your SSD. Otherwise, you can try manufacturers software to securely erase your drive. Some examples of SSD manufacturer software that’s used to manage the SSD are the Intel SSD Toolbox, the SanDisk SSD Dashboard, Micron SSD Management, or the Samsung Magician Software.
But how do you prove that your drive has been sanitized? You can try using data recovery software to see if the data is still accessible. Some companies perform verification of sanitization for drives, such as Kroll Ontrack. The National Institute of Standards and Technology (NIST) offers guidelines for media sanitization in a document called Special Publication 800-88, “Guidelines for Media Sanitation.” (Figure 2) The document covers media sanitization for many media types, include NVMe SSDs, iPhones and iPads, Blackberry, ATA SSDs, SCSI HDDs, USB removable media, and a few other media types.


Leave a Reply