Engineers developing products for the IoT need to plan security measures that grow more sophisticated over time to thwart attackers who get better at wreaking havoc.
Lars Lydersen, Silicon Labs
Skepticism about the Internet of Things (IoT) security seems to be high. Ironically, for many industries, the key to not being hacked is simply do not have the worst security. But many people are understandably concerned about hacks of the simple devices on which our everyday lives depend, and security researchers are calling IoT a catastrophe waiting to happen.
Today’s IoT security resembles that of quantum cryptography. Often referred to as a quantum key distribution, this elegant technology is unlike other key distribution schemes. Most key distribution schemes rely on assumptions about the computational complexity of factoring large numbers or the discrete logarithm problem. In contrast, quantum keys promise unconditional security based on the laws of physics.
Quantum cryptography is theoretically unbreakable, but a few weaknesses emerged in practice. Interestingly, no loopholes were discovered until a dedicated team was established to break into them. This experience brings several lessons about security. First, the hacking of quantum cryptography showed the importance of upgradable security. When the successful penetrations, called blinding attacks, were discovered, system vendors were given a grace period to patch the vulnerabilities. It turned out that the vulnerabilities could be closed via software updates. The lesson is that systems must include a means of upgrading security over their lifetime.
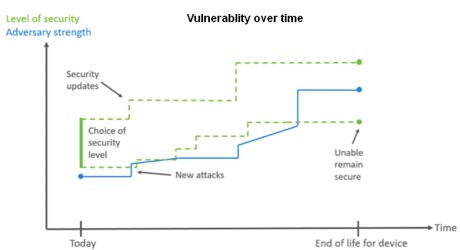
Additionally, there are always assumptions about the kind of potential adversaries security systems can defeat. Systems do not have binary security: they are not secure or insecure. The question one must ask is, Secure against what? The reality is that there are different levels of security, and a device can only be considered secure where the level of security exceeds the capabilities of a particular attacker.
Typically, the cost of security grows with the sophistication of the potential attackers. It is true that sophisticated attackers often go after more than just the compromised product itself. Business processes, physical security, and people all may be in jeopardy.
Attackers often become more capable over time, so security measures must improve as well. Hackers can discover vulnerabilities and publicize them, and hacking tools tend to spread.

In 1977, the data encryption standard (DES) algorithm was established as a standard symmetric cipher. DES used a 56-bit key size. Increases in available computational power made the cipher vulnerable to brute-force attacks, and a demonstration in 1997 revealed DES could be cracked in 56 hours. Since the early 2000s, even hobbyists on PCs have been able to break DES. With DES clearly broken, triple DES became the next standard secure symmetric cipher. Triple DES is basically running DES three times with different keys.
The advanced encryption standard (AES) has replaced DES. But even AES does not guarantee security. Though the algorithm cannot be easily broken, the implementation can be hacked in a manner analogous to what happened with quantum cryptography.
Differential power analysis (DPA) attacks are made by measuring the power consumption or the electromagnetic radiation of the circuit performing the cryptography. This side-channel data is then used to obtain the cryptographic keys. Specifically, DPA involves capturing a large number of power consumption traces followed by analysis to reveal the key.
DPA was introduced in 1998. Since then, companies like Cryptographic Research Inc. (now Rambus) have sold DPA attack tools, though at prices out of reach for most hobbyists and researchers. But today, hardware tools for advanced DPA attacks go for less than $300, and advanced post-processing algorithms are available free online. Thus, the ability to conduct DPA attacks has migrated from nation-states and wealthy adversaries to nearly any hacker.
Consider these events in the context of IoT-device longevity. A typical device for the industrial IoT might last 20 years. What will a potential adversary look like in 2040? One might speculate whether it will even be human.
Now consider three example IoT applications: smart home door locks, smart home environmental sensors, and life-supporting medical devices. A smart home door lock primarily controls the perimeter of the home. The homeowner can often remotely unlock the door through a smartphone app.
It doesn’t make sense to consider nation-state attackers in the context of attacking door locks. The more likely adversaries are security researchers and advanced hackers. Advanced hackers could compromise the door to rob houses without leaving a trace. An interesting aspect of this scenario is that occupants may only belatedly realize they’ve been robbed, as has already happened in some cases.
Security researchers often publish IoT security horror stories that make end users uncomfortable with a connected door lock. The resulting hysteria has an interesting consequence: The security solution must withstand public and media scrutiny even in the face of reasonable tradeoffs. In other words, connected devices must incorporate a higher security level than what is strictly necessary.
There are other interesting considerations for smart home environmental sensors. In the broadest sense, environmental data could be used to control actuators in systems such as HVAC. The manipulation of seemingly innocuous sensor data can have a big impact. For example, suppose a triggered fire alarm automatically opens a door lock.
It can be hard to imagine up-front the impact of large-scale sensor attacks. The best practice is to assume sensor data is as sensitive as any function it controls.
In smart-home devices, two particularly interesting challenges come up: commissioning and longevity. The install process directly impacts ease-of-use. Product developers have historically made many tradeoffs between security and usability with some such tradeoffs only identified after the product is in service. The fact that smart-home devices can remain installed for decades is an argument for giving them much higher security than may seem warranted the day they go into service.
The longevity of smart-home devices raises the question of backward compatibility. Consumers want assurances of future support and may become upset if support is suddenly removed. The best strategy is to provide a means of upgrading to the latest security protocols in the field. But this may not always be possible. Hardware constraints may prevent it – upgraded protocols may demand hardware capabilities beyond what was available at the time of the product release.
Medical device security is particularly interesting. From a safety perspective, medical devices demand strict testing and processes. But their security requirements may have been minimal. Moreover, this class of devices has already seen a number of hacks.
Nation-state security may be the right adversary class for a medical device. One reason: The potential is there for hacking these devices as an untraceable way of assassinating important individuals. What is certain is that the security of these devices will be subject to standards and certifications that will, hopefully, take such risks into account.
Regulatory and standards initiatives
The regulatory and standards initiatives around IoT security are too extensive to cover here, but two key elements must be mentioned: incentive and scalability.
Vendors have conflicting interests and may have incentives to reduce device security below what is a reasonable level for society. So security regulations must incorporate ways to incentivize without thwarting innovation. A point to note is the approach taken by GDPR, the General Data Protection Regulation now enforced by the EU. GDPR fines companies that lose valuable data serves as an incentive without limiting how the companies secure their data. This approach can serve as an inspiration for IoT security regulations.
For the foreseeable future, there will not be enough security engineers in the world to secure IoT devices. Thus any IoT security scheme must be scalable. Scalability is one of the key promises of the Platform Security Architecture (PSA) from Arm.
The PSA solves the problem of scalability through a balanced certification scheme and use of off-the-shelf secure components. This approach should make it possible for those without extensive security backgrounds to evaluate vendors based on certifications and to implement secure solutions using the components. The biggest challenge for PSA is its ties to an IP-vendor. As such, it is unlikely to be acceptable for broad standardization, even if it implements a good strategy for scalability.
In all, different types of IoT devices and applications require different levels of security. The types of adversaries and the longevity of the deployed product or system can determine the appropriate security level for a given IoT application. Ultimately, security certification schemes like Arm PSA and industrywide standardization will help secure IoT devices from attacks in the longer term.


One way to make brute force attacks take much more time would simply be to add a ten second delay after each incorrect effort, before any input would be accepted. That would be simple and cheap and not require any hardware change. It would not impact normal use at all. It would not be an ultimate solution but it could make one form of attack much slower.