LoRa (long-range) technology ensures reliable long-range communication between a node and gateway, making it well-suited for a range of Internet-of-Things (IoT) applications. The purpose of building a LoRa node is to reduce costs while ensuring long-term, low-power use for devices. LoRa’s low power is affected by several features, covered below. Features Smart programming. The written […]
Featured
What are the challenges when testing chiplets?
Chiplet testing begins with performance simulations during the design process. Compared with monolithic devices, heterogeneous chiplets require more complex testing, including known good die (KGD) testing, final test, and system level test. Success also depends on the implementation of design for test (DfT) based on several IEEE standards. Chiplet designers need high-speed tools that can […]
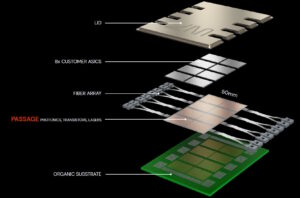
How can in-package optical interconnects enhance chiplet generative AI performance?
Generative artificial intelligence (AI) requires rapid and continuous movement of large amounts of data. In a growing number of instances, electrical input/output (I/O) connections between the ICs in chiplets are becoming a bottleneck to higher performance. Key electrical I/O performance barriers include power efficiency, bandwidth, and latency. This FAQ looks at the anticipated benefits of […]
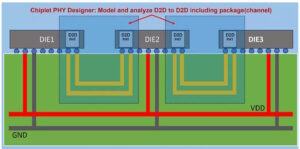
How do UCIe and BoW interconnects support generative AI on chiplets?
The bunch-of-wires (BoW) and Universal Chiplet Interconnect Express (UCIe) standards provide designers with tradeoffs in terms of throughput, interconnect density, delay, and bump pitch. This FAQ compares the performance of BoW and UCIe and looks at how optical interconnects may provide a path to even higher performance interconnects in chiplets. To realize optimal performance for […]
What is the heterogeneous integration roadmap, and how does it support generative AI?
The heterogeneous integration roadmap (HIR) is an ongoing initiative of the IEEE Electronics Packaging Society. It’s a living document that continues to evolve and expand in response to technological developments like the growth of generative artificial intelligence (AI) and quantum computing. This FAQ starts with a brief overview of heterogeneous integration, looks at the scope […]
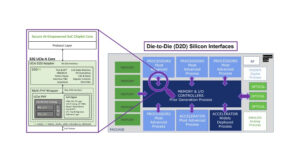
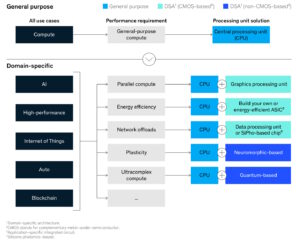
How does the open domain-specific architecture relate to chiplets and generative AI?
The Open Domain-Specific Architecture (ODSA) is a project within the Open Compute Project (OCP) community to establish open physical and logical die-to-die (D2D) interfaces for chiplets. The goal is to democratize the design and use of chiplets for domain-specific high-performance computing (HPC) applications like generative artificial intelligence (AI). Domain-specific architectures (DSAs) are an emerging approach […]
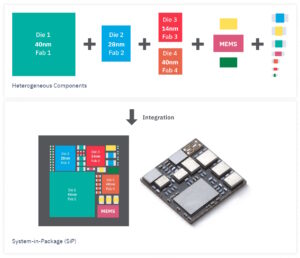
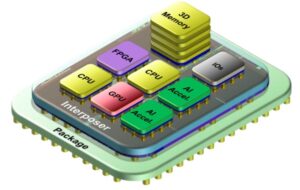
How do heterogeneous integration and chiplets support generative AI?
Chiplets are here, and more are coming. They can overcome the yield limitations of large ASICs, support a mix-and-match strategy for heterogeneous semiconductor IPs and multiple process nodes, improve thermal performance, and speed time to market. They are being used in a range of high-performance computing (HPC) applications, notably generative artificial intelligence (AI) and machine […]
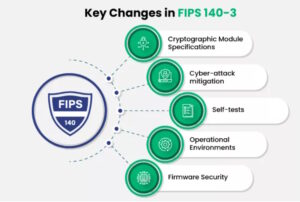
Securing devices for the IoT – FIPS 140-3 and common criteria
For developers of IoT devices and networks, the Federal Information Processing Standard (FIPS) 140-3 and the Common Criteria (CC) serve different but complementary functions. FIPS 140-3 is designed for validating software and hardware in cryptographic modules, while CC is designed to evaluate security functions in IT software and hardware. In both cases, there are related […]
Securing devices for the IoT — IEC 62443, SESIP, and PSA
The International Electrotechnical Commission (IEC) 62443 series of standards is focused on security for Industrial Automation and Control Systems (IACS); the Security Evaluation Standard for IoT Platforms (SESIP) provides a method for trustworthy assessment of the security IoT platforms, including the industrial IoT (IIoT), and Platform Security Architecture (PSA) certification requires strict adherence to the […]
Securing devices for the IoT – managing memory
Memory management is important in all digital electronic devices including devices designed for use on the Internet of Things (IoT). It supports efficient resource allocation and memory utilization and prevents memory fragmentation, improving efficiency. It also supports memory protection and device security. This FAQ briefly reviews the common weakness enumeration (CWE) scheme for identifying software […]