The International Electrotechnical Commission (IEC) 62443 series of standards is focused on security for Industrial Automation and Control Systems (IACS); the Security Evaluation Standard for IoT Platforms (SESIP) provides a method for trustworthy assessment of the security IoT platforms, including the industrial IoT (IIoT), and Platform Security Architecture (PSA) certification requires strict adherence to the defined architecture.
While these standards are developed and maintained independently, they are also somewhat interrelated. This FAQ reviews the IoT standards and their interrelationships.
The IEC-62443 series provides a systematic approach to assessing the need for cybersecurity in industrial systems. It considers factors from initial risk assessments to ongoing operations and defines five security levels (SLs) from SL0 (no security) to SL4 (resistant against nation-state attacks). SL3 and SL4 require hardware-based security. Discrete ICs for hardware security are temper-resistant and provide higher security levels than software-based solutions, as seen in Figure 1.
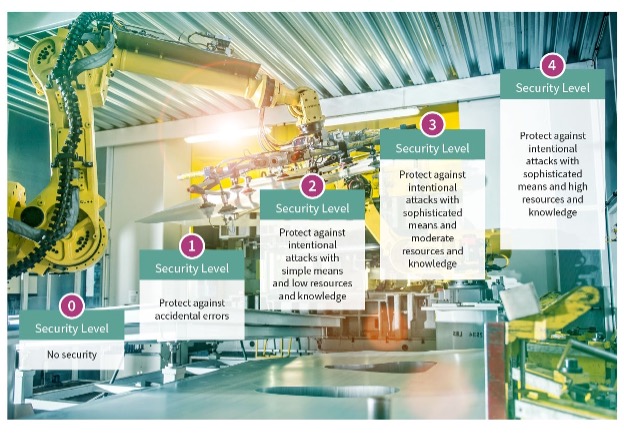
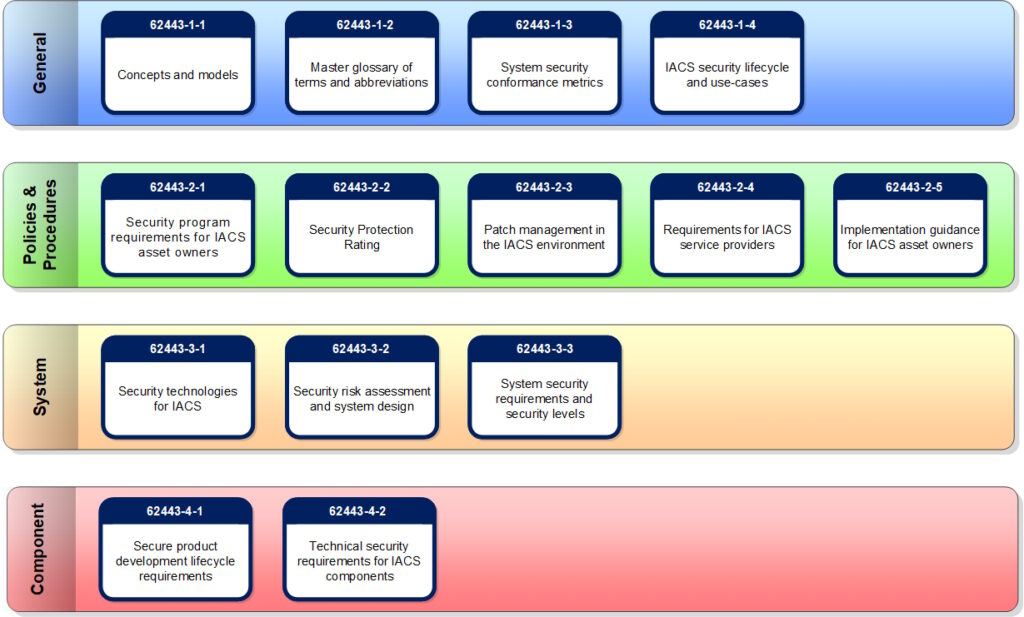
Figure 2 shows that the various sections of the IEC 62443 standard can be split into four general categories:
- General documents introduce basic concepts of industrial security and provide an overview of related processes.
- Policies & Procedures documents review the importance of proper security policies and suggest several useful procedures to be followed.
- System documents review essential considerations for integrating security into IACS at the system level.
- Components documents detail the security requirements for individual components and sub-systems that comprise an IACS.
SESIP
SESIP is based on the Common Criteria methodology (ISO 15408-3) and defines a standard for trustworthiness assessment of the security of the IoT platforms. SESIP is focused on security for individual IoT nodes. It defines a platform security architecture (PSA), security assurance requirements (SARs), and Security functional requirements (SFRs). It includes some flexibility for implementation. For example, a subset of the SFRs may be identified for a specific application that requires higher assurance.
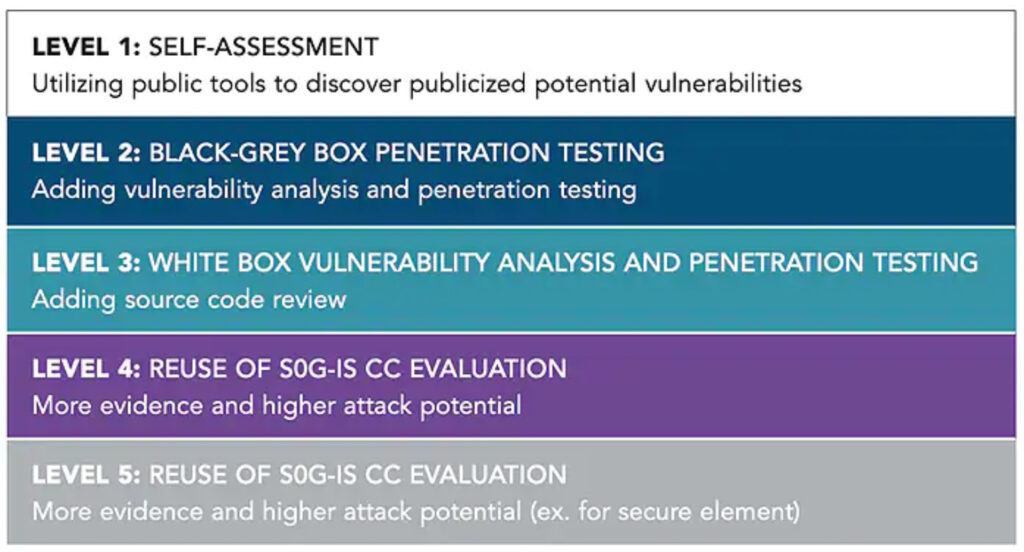
SESIP platforms, also called profiles, are being developed for specific use cases like ARM PSA L1 and IEC 62443. SESIP includes five assurance levels from SESIP1 to SESIP5 as follows in Figure 3:
- SESIP1 is a self-assessment without third-party validation.
- SESIP2 adds black-box penetration testing and vulnerability testing.
- SESIP3 uses a more detailed white-box vulnerability analysis and penetration testing, including a source code review.
- SESIP4 is for the re-use of senior officials’ group information systems security (SOG-IS) certified platforms or sub-systems by licensed third-party evaluation laboratories.
- SESIP5 adds that all the standard Common Criteria assurance components must be included in the assessment and specifically requires AVA_VAN.5 advanced methodical vulnerability analysis.
PSA
ARM, a co-founder of the PSA-Certified organization, created the PSA specifications. While SESIP allows some flexibility in implementation, PSA certification requires strict adherence to the platform’s security functional requirements. A key element in PSA chip-based security is the PSA root of trust (PSA-RoT).
The PSA-RoT is a secure processing environment based on a Protection Profile and an independent evaluation. It combines trusted hardware like crypto accelerators, private key stores, and memory with firmware separated from the system software using hardware isolation. To gain ‘PSA Certified’ status, the PSA-RoT must be subjected to trustworthy testing by an independent testing laboratory.
The three levels of PSA certification include:
- PSA Certified Level 1 focuses on 50 requirements split into three sections for chip vendors, software platforms, and device manufacturers. It maps to the requirements of NISTIR 8259A (see references) and ETSI EN 303 645 Cybersecurity Standard for Consumer IoT Devices.
- PSA Certified Level 2 — protection from scalable software attacks adds a 25-day independent evaluation of the chip’s PSA-RoT using the published Protection Profile, Evaluation Methodology, and Attack Methods.
- PSA Certified Level 3 — protection from substantial physical and software attacks adds deeper security testing of PSA-RoT assets, including side-channel attack protection for cryptographic keys.
Summary
Securing devices for the IoT and IIoT is complex. Fortunately, several standards are available to guide the development of secure and robust IoT devices. Depending on the application and circumstances, developers can turn to IEC 62443, SESIP, and PSA for the requirements for designing secure IoT devices.
References
How to implement IEC 62443, Infineon
Level 3 PSA Certification – What it is and Why it Matters, Silicon Labs
SESIP: An optimized security evaluation methodology, designed for IoT devices. Global Platform
SESIP System-Level Security for IoT Applications, NXP
Structuring the ISA/IEC 62443 Standards, ISA Global Cybersecurity Alliance
What is NISTIR 8259A?, Firmalyzer
What Is the PSA Certified IoT Security Framework?, PSA Certified


Leave a Reply