An attack surface is the sum of all the attack vectors or ways that an attacker can gain malicious access to a network or system. The growth in remote work and the adoption of cloud services have increased the number of attack vectors and the size of the attack surface for most organizations and applications.
This FAQ reviews the different types of attack surfaces, looks at some of the more common attack vectors, and closes with a brief review of how Attack Surface Management (ASM) and Cloud Native Application Protection (CNAPP) can be used to address enterprise security challenges.
Historically, the attack surface has been divided into three segments: the digital attack surface, the physical attack surface, and the social engineering attack surface. More recently, two new attack surfaces have emerged, the artificial intelligence (AI) attack surface and the Internet of Things (IoT) attack surface, and more continue to appear (Figure 1):
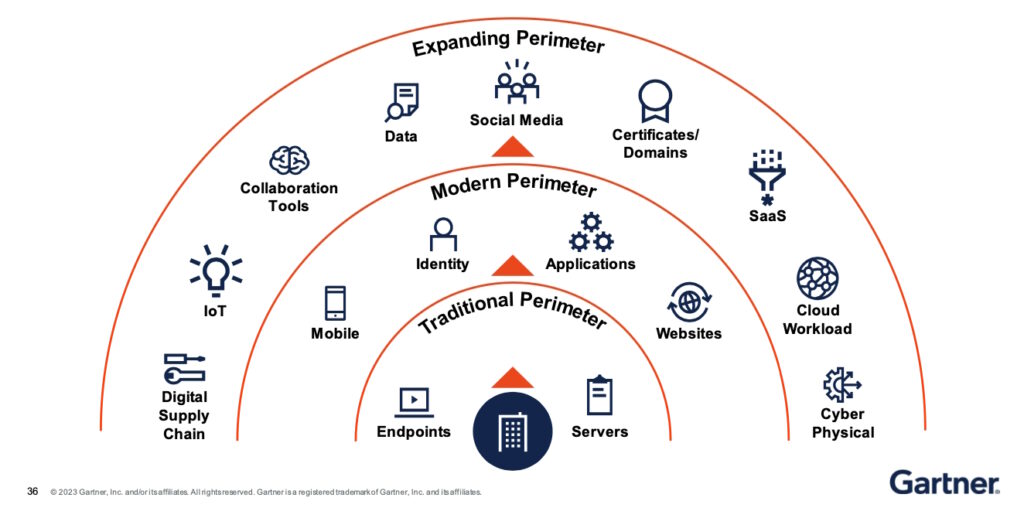
- Digital attack surface includes all external vulnerabilities accessible through the internet like system access points, websites, ports, and services.
- Physical attack surface is all access points into the network hardware, including equipment on-premises, equipment connecting to the network from outside, and malicious employees that share access to unauthorized individuals.
- Social Engineering attack surface includes malicious individuals posing as employees to gain information, capturing credentials through a phishing technique, or sending infected files to an employee.
- AI attack surface takes advantage of inherent weaknesses in AI systems like their vulnerability to being manipulated by specially engineered data posted to the system. They can also be attacked using a technique called adversarial machine learning, that can identify unanticipated security weaknesses in systems.
- IoT attack surface can be surprisingly dangerous. IoT devices are often small like wireless sensors, but hacking into them can cause false readings to be sent to control equipment, potentially affecting production, or damaging large and expensive machinery. Other IoT devices are important for facility security. The large numbers and variety of IoT devices can provide an attractive target for gaining access to the wider network.
Types of attack vectors
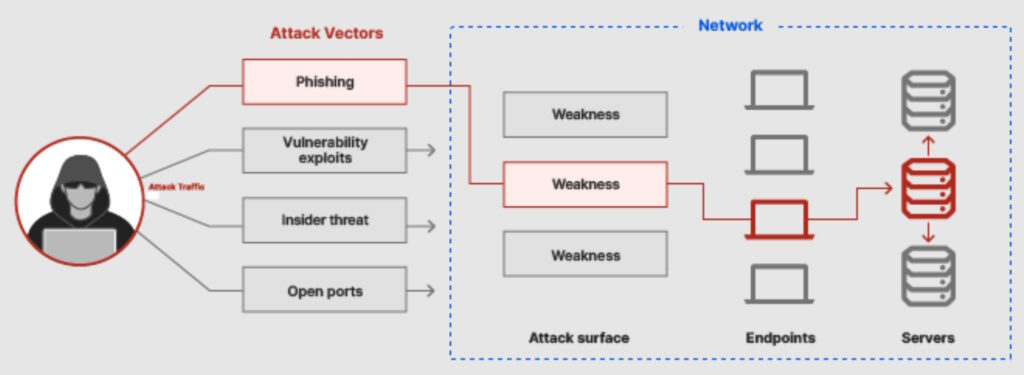
There can be hundreds of potential attack vectors and large attack surfaces for major operations. Security is a continuous process, especially in large organizations where new software, applications, websites, and hardware are constantly appearing or evolving. The common types of attack vectors can be obvious or common sense, but they continue to threaten network security including:
- Compromised credentials like weak or unprotected passwords
- Phishing attacks or other ways to manipulate employee behavior to grant access to an unauthorized individual
- Malicious and disgruntled employees who intentionally share credentials or sensitive data
- Poor encryption implementations like expired SSL certificates and unpatched data transfer protocols
- Excessive traffic from distributed denial of service (DDoS) attacks
- Misconfigured infrastructure or services
- Unsecured connection with third parties like vendors or customers
Protection options
ASM and CNAPP are designed to solve different challenges related to enterprise security. ASM is a broad-based analysis of all available network resources and cyber assets. It considers every aspect of security from edge devices to the cloud. ASM can be used to define an organization’s attack perimeter and all the vulnerable attack surfaces. ASM aggregates every aspect of the system into a holistic security analysis.
CNAPP is a focused dive into all aspects of a public cloud infrastructure. While ASM provides a broad analysis of internal threat surfaces, CNAPP focuses on finding security issues related to cloud infrastructure and associated services like AWS and Microsoft Azure. CNAPP tools check cloud configurations and scan for misconfigurations and vulnerabilities.
Summary
Minimizing attack surfaces is an important element in IoT and general network security. It involves identifying and minimizing or eliminating the attack vectors that comprise the attack surface. The number and types of attack surfaces and attack vectors are growing, increasing the challenges for security engineers. Tools like ASM and CNAPP are available to help analyze networks and identify potential attack vectors and threat surfaces.
References
8 Immediate Actions to Reduce the Cyber Attack Surface, Cybeready
How do I Reduce My Attack Surface?, Armis
The IoT Attack Surface: Threats and Security Solutions, Trend Micro
Understanding the differences between Cloud Native Application Protection Platforms and Attack Surface Management, JupiterOne
What Is An Attack Surface?, Fortinet
What is an attack surface?, IBM
What is an Attack Surface? (And the Best Way to Reduce It), StrongDM
What is an attack vector?, CloudFlare



Leave a Reply