Over-the-air (OTA) updating of firmware and software on Internet of Things (IoT) devices is a requirement, not an option. The large number of IoT devices makes manual updates impractical and even dangerous.
This FAQ reviews two key tools for managing and implementing OTA for IoT devices: open-source standards for managing resource-constrained devices and industry standards for updating the firmware and software on IoT devices.
Open-source standards for managing constrained IoT devices
The Lightweight M2M (LwM2M) open-source standard from the Open Mobile Alliance SpecWorks (OMA) is built on the success of the Alliance’s OMA device management (OMA DM) standard. LwM2M was designed to reduce power consumption and data requirements to support managing devices with limited processing and storage capabilities (called resource-constrained devices). It supports low-power wireless networking protocols. LwM2M includes datagram transport layer security (DTLS) that’s designed to prevent eavesdropping, tampering, or message forgery. It uses the Constrained Application Protocol (CoAP), a specialized web transfer protocol for use with constrained devices on networks with low bandwidth and low availability (Figure 1).
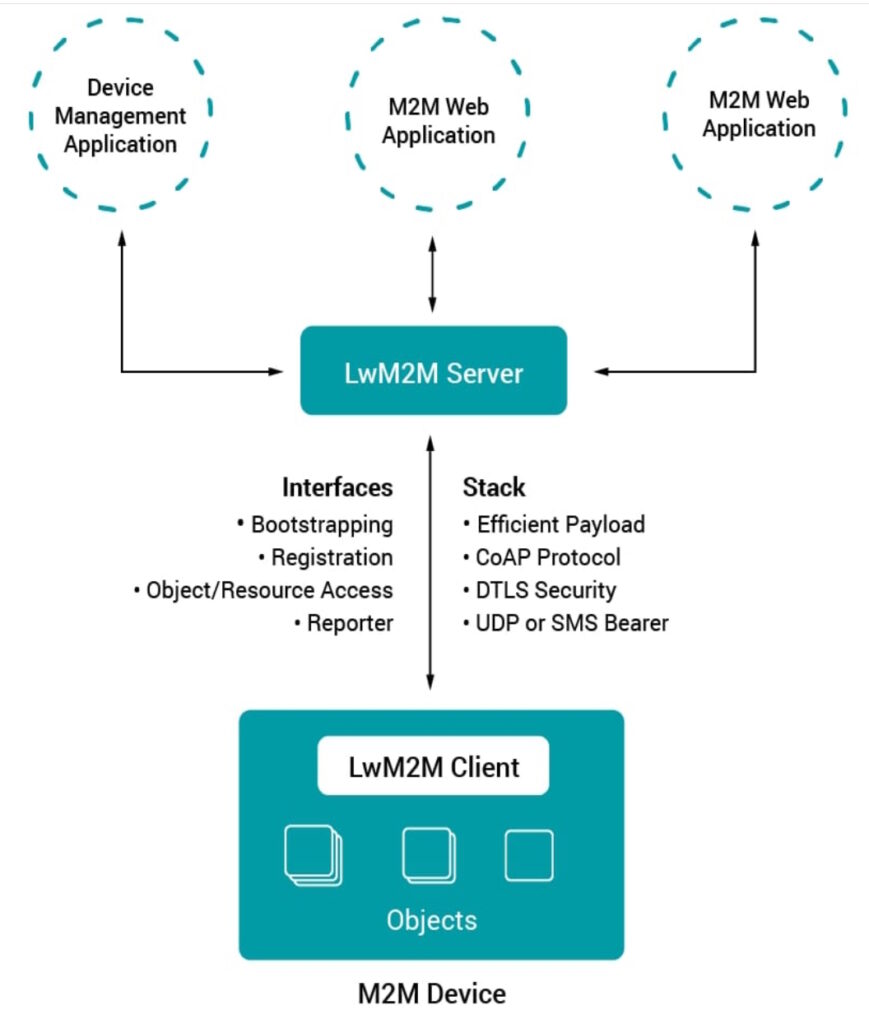
The CoAP management interface (CoMI) is another option for communications with resource-constrained devices. The Internet Engineering Task Force (IETF) Constrained RESTful Environments (CoRE) working group has standardized CoMI and added functions to make it more suitable for IoT and M2M applications like smart energy and building control networks. It has been optimized to handle installations with large numbers of devices where the messages are infrequent and as small as possible.
Technical Report 069 (TR-069) from the Broadband Forum uses the CPE WAN Management Protocol (CWMP) and defines an application layer protocol for remote management and provisioning of customer-premises equipment (CPE) connected to an Internet Protocol (IP) network. TR-069 supports functions for auto-configuration, software, or firmware image management, plus software modules, status and performance management, and diagnostics. CWMP is a bidirectional Simple Object Access Protocol (SOAP)- and HTTP-based protocol. It’s designed for use with a variety of Internet access devices like gateways, modems and routers, and endpoint devices in the IoT.
Update frameworks
Update frameworks are important tools to support secure connectivity. For example, the Software Updates for Internet of Things (SUIT) from the IETF is a firmware updating solution for constrained devices with about 10 kB of RAM and up to 100 kB of FLASH memory. SUIT is currently being defined, and the SUIT working group (WG) has completed two documents:
- An IoT firmware update architecture.
- An information model for the SUIT manifest.
For the next step, the SUIT WG will be using the Concise Binary Object Representation (CBOR) data format that supports extremely small code size and small messages and the related CBOR Object Signing and Encryption (COSE) protocol to encode SUIT messages.
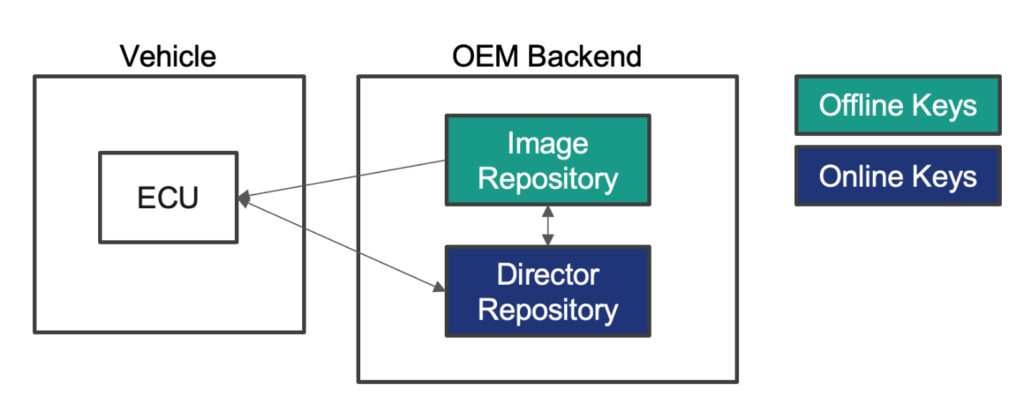
The Uptane Alliance has developed its eponymous software update security standard for automotive applications. The Uptain framework assumes that these systems will get compromised and uses multiple layers of security and separation of roles to eliminate single points of failure that might result from any compromise of the system.
For example, Uptane uses two separate data repositories, the image repository, and the director repository, with different signing authorities. Offline keys, which are signed by a root signing authority, are used to sign images sent to the electronic control units (ECUs) and provide high levels of security. The director repository uses online keys for greater flexibility. The director repository can coordinate software updates with multiple ECUs (Figure 2).
Blockchain technology is another possibility for implementing a secure update framework. CHAINIAC has been proposed as a decentralized software update framework that eliminates single points of failure and supports verifiable integrity and authenticity for software updates. For example, to achieve tamper evidence, consistency, and search efficiency of the timeline and enable a secure rotation of signing keys, CHAINIAC uses skipchains, authenticated data structures that combine the attributes of skip lists and blockchains.
Summary
Designers responsible for IoT device deployments have numerous choices of open-source standards for managing resource-constrained devices like wireless IoT nodes and for managing the delivery of software and firmware updates to those devices.
References
A Secure Software Update Framework for Automobiles, Uptane
CHAINIAC: Proactive Software-Update Transparency via Collectively Signed Skipchains and Verified Builds, International Association for Cryptologic Research
LwM2M — Lightweight M2M standard — protocol and its benefits, AVSystem
Over-the-Air Updates for IoT: What They Are and How to Approach Them, Particle
Secure Firmware Updates in the IoT, Competence Centre for ITSecurity at FH Campus Wien
Secure IoT Firmware Updates Are a Necessity for Resilient IoT Deployments, Venafi
Securing Automotive Over-the-Air Software Updates, Renesas
Software Updates for Internet of Things (suit), IETF
The Key to Firmware Security in Connected IoT Devices, Keyfactor
Uptane: Securing Software Updates for Automobiles, Uptane



Leave a Reply