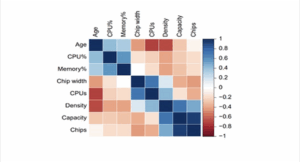
Silent data corruption (SDC), sometimes called bit rot or silent data errors (SDEs), refers to errors in data that are not detected by standard error-checking mechanisms, leading to potentially significant data loss or incorrect calculations. SDCs can lead to inaccurate training, incorrect predictions, and unreliable performance. Detecting SDC requires specialized techniques and tools. SDCs can […]
FAQ
How can neuromorphic devices be harnessed in edge AI computing?
Neuromorphic computing, which mimics the human brain’s architecture and function, can be leveraged in edge computing to improve power efficiency, speed, and adaptability. By processing data locally and using event-driven computation, neuromorphic chips can optimize resource usage in edge AI applications, reducing reliance on centralized cloud processing. Spiking neural networks (SNNs) are the most common […]
What is ‘compute-in-memory’ and why is it important for AI?
If you are running AI workloads, here is something that might surprise you. Your processors are wasting more energy shuffling data around than actually doing the calculations you care about. This inefficiency is becoming a serious limit for the next generation of artificial intelligence systems. As neural networks grow to billions of parameters, traditional von […]
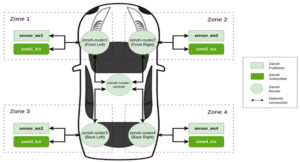
How does the Zenoh protocol enhance edge device operation?
Zenoh is an open-source platform that manages data in transit and at rest across the entire edge-to-cloud continuum, as well as facilitates computations on edge devices. Targeted applications include robotics, automotive, and IoT. Its low overhead makes it compatible with low-power or bandwidth-limited networks like LPWAN, LoWPAN, and Bluetooth Low Energy (BLE). Zenoh is primarily […]
How do AI agents and model context protocol work together?
An AI agent, combined with a model context protocol (MCP), can create more contextual AI systems that can perform a wide range of tasks, from automating processes to providing insights and interacting with users. MCP helps AI agents connect to data sources, enabling them to access information, collaborate with other systems, and make decisions based […]
What is the math of negative feedback and how is it used to ensure stability?
Negative feedback can create a control system where the output of a process is used to counteract any deviations from a desired set point, effectively “correcting” the system, bringing it back to equilibrium, and maintaining stable operation. It’s used in a variety of applications, including voltage regulation, temperature controllers, audio amplifiers, and operational amplifiers. This […]
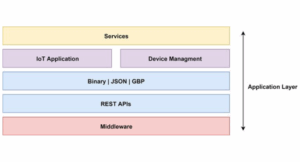
What are the different key layers of IoT architecture? part 2
This second part of the FAQ discusses the three upper layers of the IoT architecture, which extend beyond the physical and network layers. The middleware layer processes and manages raw IoT data from connected devices. The application layer provides user interfaces and visualization tools. The business layer converts technical capabilities into actionable business outcomes. Part […]
What are the different key layers of IoT architecture? part 1
A layered Internet of Things (IoT) architecture provides modularity, scalability, and flexibility, allowing each layer to focus on specific tasks and technologies. This FAQ series covers the five-layer IoT architecture and explains why it is a commonly used framework. This first part focuses on the first two layers. IoT Architecture provides a structured framework for […]
Five challenges for developing next-generation ADAS and autonomous vehicles
ADAS and autonomous vehicles need new datacom architectures and new attitudes. The state of California requires autonomous vehicle manufacturers to annually document and report every manual intervention by test drivers, including the cause and the vehicle’s mileage. In less than five years, these reports have demonstrated significant improvements in miles per intervention for virtually every […]
What is the HPC memory wall and how can you climb over it?
The high-performance computing (HPC) memory wall generally refers to the growing disparity between processor speed and memory bandwidth. When processor performance outpaces memory access speeds, this creates a bottleneck in overall system performance, particularly in memory-intensive applications like artificial intelligence (AI). This article begins by exploring the conventional definition of the memory wall and then […]