Security is an important concern for developers of all types of systems. This FAQ reviews several important security standards for IoT cyber security, security vulnerabilities in industrial automation and control systems, standards for analyzing and identifying secure coding errors in C applications, and concepts of application software security and levels of trust.
The European Telecommunications Standard Institute (ETSI) EN 303 645 was developed to provide the foundation of the basic-level IoT assurance under the EU Cybersecurity Act (CSA). It’s a globally-recognized standard for consumer IoT cyber security. The standard is based on 14 high-level recommendations, used to establish 68 provisions, 33 mandatory requirements, and 35 recommendations (Figure 1).
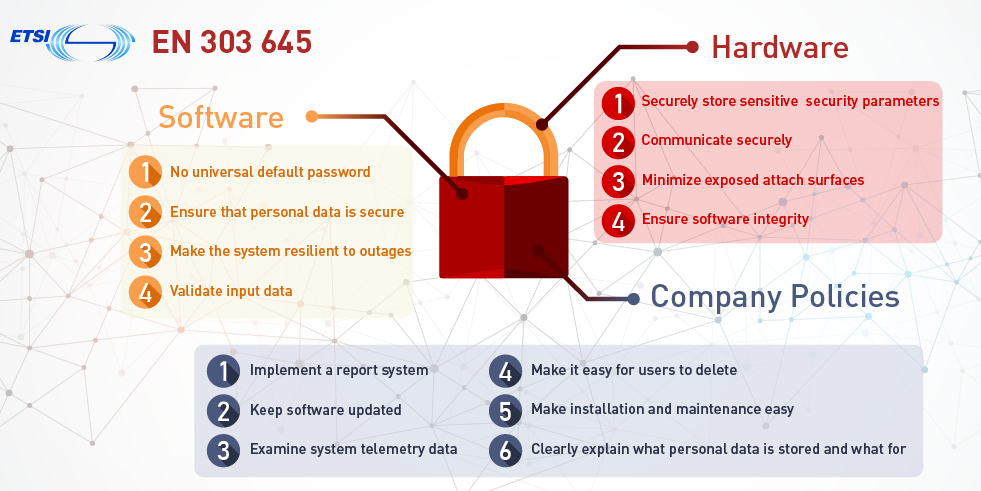
ETSI EN 303 645 is designed to help prevent large-scale attacks against smart devices, including children’s toys and baby monitors, connected safety-relevant products such as smoke detectors and door locks, smart cameras, TVs and speakers, wearable health trackers, connected home automation and alarm systems, connected appliances, and smart home assistants. Compliant devices are expected to successfully resist distributed denial of service (DDoS) attacks or hijacking the devices to mine cryptocurrency or spy on users.
ETSI has also released a test specification, ETSI TS 103 701 (Cyber Security for Consumer Internet of Things: Conformance Assessment of Baseline Requirements), that describes how a structured and comprehensive conformity assessment is to be performed. This test specification is designed to be used by manufacturers, vendors, and distributors to assess the compliance of devices to ETSI EN 303 645 in self-assessments or via testing labs.
Industrial automation and control systems
ISA/IEC 62443 is a series of standards that provide a flexible framework to address and mitigate security vulnerabilities in industrial automation and control systems (IACSs). For example, one standard in the series, ISA 62443-4-2 (Security for Industrial Automation and Control Systems: Technical Security Requirements for IACS Components), provides the cybersecurity technical requirements for the embedded devices, network components, host components, and software applications that make up an IACS. The standard, based on the IACS system security requirements of ISA/IEC 62443-3-3 (System Security Requirements and Security Levels), specifies security capabilities that enable a component to mitigate threats for a given security level without the need for additional countermeasures.
ISA 62443-4-2 followed ISA/IEC 62443-4-1 (Product Security Development Life-Cycle Requirements), which defines the process requirements for the secure development of devices and products used in an IACS and defines a secure development life cycle for maintaining those secure devices and products. The life cycle structure includes:
- Definition of security requirements
- Secure design parameters
- Secure implementation requirements (including coding guidelines)
- Security verification and validation
- Managing defects
- Managing software patches
Analyzing secure coding in C
ISO/IEC TS 17961 was developed to establish baseline requirements and rules for analyzers, including static analysis tools and C language compilers needed to identify insecure code beyond the requirements of the language standard. The criterion for selecting the rules is that their implementation must Identify secure coding errors without generating excessive false positives. ISO/IEC TS 17961 was also developed to complement other C language standards and guidelines, and it’s the only publication targeted at code analyzers, not developers (Table 1). A qualifying analyzer has to detect any violation of any of the rules and produce a diagnostic for each rule in the violated specification. If a program being analyzed violated multiple rules, a qualifying analyzer must produce at least one diagnostic notice and may optionally provide aggregated diagnostics for all violated rules.
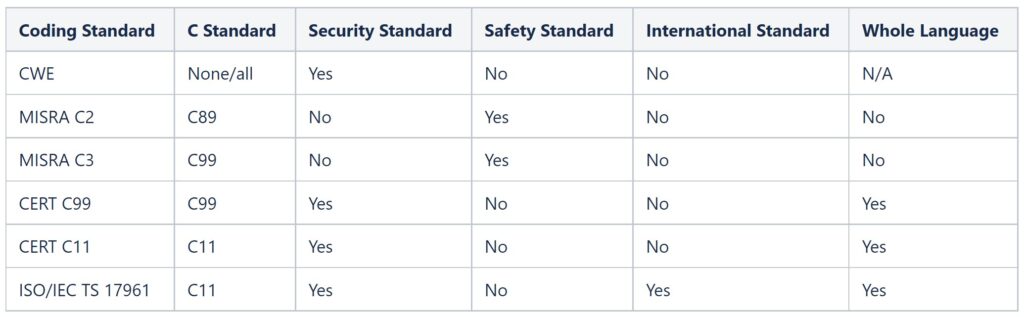
The basic rules may be extended to suit the needs of specific applications as needed to provide a minimum performance guarantee for device users. ISO/IEC TS 17961 includes code examples for each basic rule. Noncompliant code examples are also included to demonstrate language constructs that have weaknesses with potentially exploitable security implications. The examples of exploitable code produce a diagnostic alert from a qualifying analyzer. Compliant examples should not produce a diagnostic from a qualifying analyzer.
Application code security
The ISO 27034 standard is focused on application security. It defines specific concepts, terms, and activities to develop a comprehensive approach to application code security, including:
- Application Security Control (ASC)
- Application Level of Trust (ALT)
- Organization Normative Framework (ONF)
- Application Normative Framework (ANF)
- Application Security Verification Process (ASVP)
The ASC is one of the base concepts of ISO 27034 and is designed to prevent a security weakness in an application. ASCs are sometimes referred to as application security requirements. For example, SQL injections are a common application security weakness and can be addressed in ISO 27034 by using binding variables in SQL statements. Each ASC is based on application use, such as the use of binding variables in SQL statements in an application that uses databases, and context, such as the need to mask credit card numbers on the screen to meet the requirements of the Payment Card Industry Data Security Standard (PCI DSS). Each ASC must also include a verification method such as running a scanning tool to identify SQL vulnerabilities.
Application Level of Trust
Not every application needs the same level of security. External web-based applications that interact with personal data require a higher level of security than internal applications with no access to sensitive information. Each ASC is defined relative to one or more levels of trust. For example, a financial institution may use three ALTs:
- Level 0 may include only ASCs that mitigate the highest risks
- Level 1 would include more ASCs than Level 0 and mitigate against additional risks
- Level 2 would include even more ASCs and mitigate against the highest number of risks
Each ASC has a predefined expectation for its ALT. Once developed, each application is audited to measure its actual ALT to identify ASCs with lower actual ALTs than specified. The combination of ALT specifications and audits ensures that any security shortcomings can be addressed before the ASC goes into the field.
Organization normative framework
The ONF is an organization-wide collection of ASCs and processes called the ASC Library. It defines when and how an application should use specific security testing, such as penetration testing. It includes an “application life cycle security reference model” with a scope beyond just software security and defines planning, building/buying, testing, and using decommissioning applications and related infrastructure. Another purpose of the ONF is to define when a specific ASC is used.
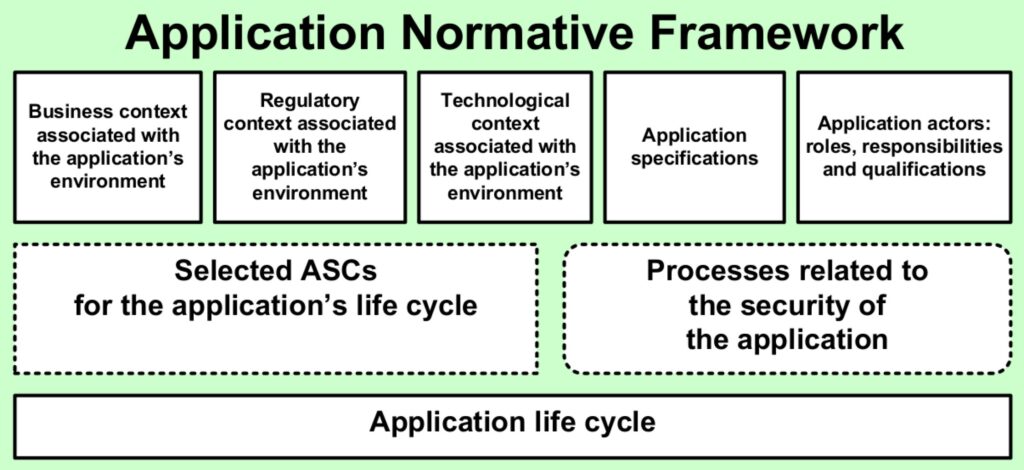
Application normative framework
An ANF is the set of ASCs and application security processes that apply to a particular application and is a subset of the ONF. For example, a financial institution may have over 50 different ASCs with different combinations of ALTs that require various forms of threat modeling and code reviews. An ANF can also describe the ASC development process, plus its operational and decommissioning processes (Figure 2).
Application security verification process
Finally, ISO 27034 includes the requirement for a formal ASC security verification process. Code reviews, penetration testing, and other aspects of security verification are directly related to individual ASCs. Prior to ISO 27034, security verification was a more generic process that did not necessarily consider the specific ALTs and other performance requirements of individual ASCs.
Summary
In today’s connected world, security is an important aspect of the development process. This FAQ has reviewed some of the major security standards for IoT cyber security, security vulnerabilities in industrial automation and control systems, standards for analyzing and identifying secure coding errors in C applications, and concepts of application software security and levels of trust, as found in ETSI EN 303 645, ISA/IEC 62443, ISO/IEC TS 17961, and ISO 27034, respectively.
References
ETSI EN 303 645 – Cyber Security for Consumer Internet of Things: Conformance Assessment of Baseline Requirements, ETSI
IOT security for EN 303 645, Ineltek
ISA/IEC 62443 standard specifies security capabilities for control system components, International Society of Automation
ISO/IEC 27034-2:2015, ISO
ISO/IEC TS 17961:2013, ISO
ISO/IEC TS 17961 C Secure Coding Rules, Carnegie Mellon University
The Beginner’s Guide to ISO 27034, Security Compass