For developers of IoT devices and networks, the Federal Information Processing Standard (FIPS) 140-3 and the Common Criteria (CC) serve different but complementary functions. FIPS 140-3 is designed for validating software and hardware in cryptographic modules, while CC is designed to evaluate security functions in IT software and hardware. In both cases, there are related standards from the International Standards Organization (ISO) and the International Electrotechnical Commission (IEC).
FIPS testing is a prerequisite for CC certification since all security products covered by CC include hardware cryptographic modules. FIPS 140-3 aligns with the ISO/IEC 19790 standard for Security Requirements for Cryptographic Modules, and ISO/IEC 24759 specifies the test methods to be used to confirm that a cryptographic module conforms to ISO/IEC 19790.
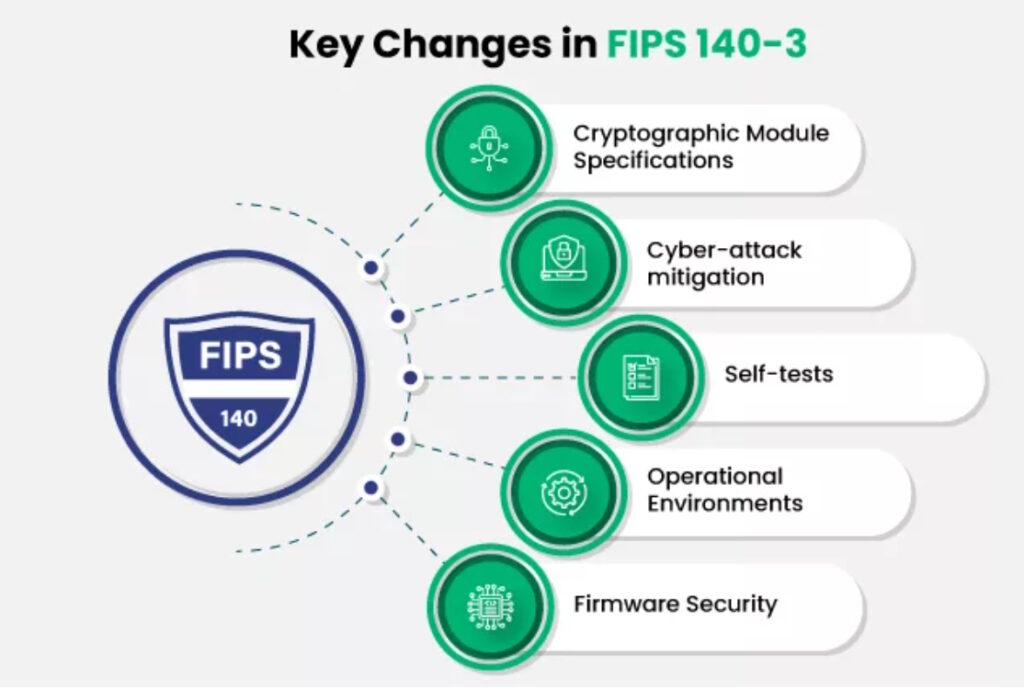
When FIPS 140-3 was published in 2019, a five-year sunset period was announced for FIPS 140-2 certificates. FIPS 140-3 includes enhancements in several areas, including cryptographic module specifications, cyber-attack mitigation requirements, self-tests, operational environment requirements, and firmware security (Figure 1).
The four FIPS 140-3 levels include:
- Level 1: Uses externally tested algorithms and production-grade equipment.
- Level 2: Adds role-based and physical tamper-evidence authentication.
- Level 3: Adds tamper-resistance and identity-based authentication. This level also requires the module to detect and react to out-of-range voltage or temperature, called environmental failure protection (EFP), or alternatively undergo environmental failure testing (EFT).
- Level 4: Increases the severity of the physical security requirements, including the ability to be tamper-active, and erase the contents of the device if it detects various forms of environmental attack. It must have EFP, protection against fault injection, and multi-factor authentication.
Common criteria
Each country has its own CC authority. In the U.S., CC is administered by the National Information Assurance Partnership (NIAP). CC and the Common Methodology for Information Technology Security Evaluation (CME) are the technical basis for the international CC Recognition Arrangement (CCRA).
CC is formalized in ISO/IEC 15408, Common Criteria for Information Technology Security Evaluation, a security standard that can achieve comparability between the results of independent security evaluations of IT products. Key concepts in CC include:
- Target of Evaluation (TOE) is the product or device being evaluated.
- Protection Profile (PP) identifies security requirements for a class of security devices.
- Security Target (ST) describes the security properties of the TOE and can require conformance with one or more PPs.
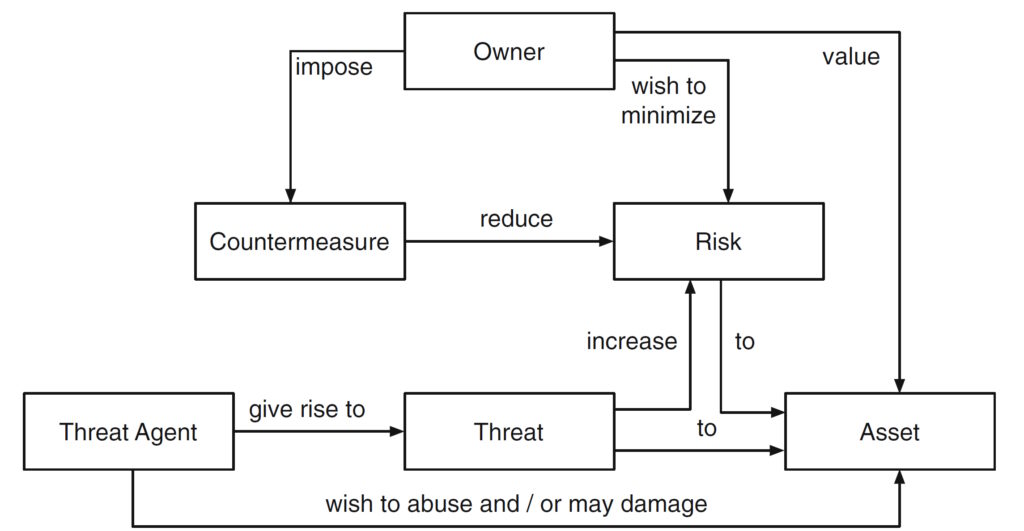
CC is based on a general security model that’s described in ISO/IEC 15408 (Figure 2). The model assumes that TOE owners want to implement countermeasures to minimize cyber risks. PPs are used to describe the security needs of a class of TOEs, like client virtual private network (VPN) applications. TOE developers publish their security claims in the form of STs. A CC evaluation determines if the ST is compliant with a specific PP.
Summary
FIPS 140-3 and CC are complementary standards for IoT cyber security. FIPS 140 is focused on validating software and hardware in cryptographic modules, while CC focuses on security functions in IT software and hardware. Both are based on a series of ISO/IEC standards, and FIPS testing is a prerequisite for CC certification.
References
A Structured Comparison of Security Standards, ResearchGate
Common Criteria, Wikipedia
Common Criteria Portal
FIPS 140-2 Vs 140-3, SignMyCode
FIPS 140-3 certification, Thales
FIPS 140-3 Security Requirements for Cryptographic Modules, Encryption Consulting
ISO/IEC 15408-1:2022: Information security, cybersecurity and privacy protection – Evaluation criteria for IT security, ISO
What is FIPS 140-3? Entrust



Leave a Reply