The popular TV drama Mr. Robot once portrayed a penetration of a building automation system. Security experts say the same exploit could have happened in real life.
Leland Teschler
Executive Editor
In 2015, TV viewers who tuned into episode five (having the catchy title “eps1.4_3xpl0its.wmv”) of a series called Mr. Robot watched the main character try to destroy magnetic tape data backups held at a facility that was portrayed as both well-fortified and remote. The plan was to slowly raise the temperature of the storage room to point where the tapes would be compromised. The means of raising the temperature was to connect an ordinary Raspberry Pi computer board into the climate control system. The Pi would simply override climate commands from the building automation controller.
In Mr. Robot, this scheme actually worked as planned. To the average viewer, the whole building-

penetration scenario probably seemed pretty simple – perhaps too simple. Of course, script writers have a reputation for playing fast and loose with facts in the interest of a compelling story. Technology-literate viewers might wonder whether the events of episode five could really unfold in real life the way writer David Iserson envisioned.
We wondered the same thing. So we contacted two cybersecurity experts with experience in building automation systems. Michael Chipley is the president of The PMC Group LLC, a firm which helps companies make their building control systems cyber-secure. Billy Rios is the founder of WhiteScope, a security consulting firm with experience in IoT and embedded device security assessments. Among other things, they run penetration tests and size up facilities for security issues.
We asked both Chipley and Rios about the events depicted in episode five.
Inside the wall
One of the scenes depicts how the Pi was introduced into the climate control network. It involves the main character, Elliot Alderson, removing a thermostat to reveal a large hole in the wall behind it. Elliot splices the Pi into the network lines coming into the thermostat, pushes the Pi through the hole in the wall, and re-mounts the thermostat.

Perhaps the most basic question about this scenario is whether or not you’ll typically find a hole behind a wall thermostat big enough to push a Pi through. After all, removing the thermostat in your home will typically reveal only a small hole big enough for a couple wires. No chance there for a Mr. Robot-style Pi hack.
But the situation can be different in commercial buildings, according to the security experts. “The holes behind these devices can be quite large,” says Billy Rios. “I don’t think inserting a Raspberry Pi behind one them would be difficult. It’s certainly not something I would worry about if I were doing something similar.”
Nevertheless, interviews given by Mr. Robot staff indicate that getting the Pi into the wall had its

challenges, though it was only done for TV. Speaking to Rolling Stone magazine, Mr. Robot chief technical adviser Kor Adana said on ordinary Pi was too big to fit through the thermostat hole and had to be modified. He explained that a network cable had to be soldered directly to the board after the removal of a “wireless network port.” (Of course, the version of the Pi available in 2015 when the show aired didn’t contain wireless capabilities. We surmise Adana was referring to the RJ45 jack for an Ethernet connection.)
The bigger question is whether a Pi added to a climate control network could legitimately cause the kind of destructive overheating depicted in Mr. Robot. The answer to the question lies in the make-up of industrial building automation protocols typically used for buildings.
Major HVAC vendors such as Honeywell and Johnson Controls have their own proprietary network protocols, and there are also standard protocols for building automation systems. Expert familiar with these protocols say they all lack security features that would recognize and isolate bogus devices.
To cite a specific example, consider BACnet, for Building Automation and Control network. It is an ASHRAE, ANSI, ISO 16484-5 standard. Some 842 HVAC vendors now use it. So it is probably a good candidate for controlling E Corp.’s Steel Mountain tape back-up facility.
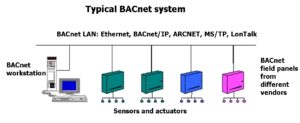 “BacNET can be implemented via serial or TCP/IP. We see both quite often. BacNET doesn’t usually provide for authentication or integrity validation, so once you get access to the BacNET, it’s game over for the building. And there are a variety of ways to get access to a building’s BacNET. The scenario shown in Mr. Robot is totally plausible, both in serial BacNET and via TCP,” says Rios.
“BacNET can be implemented via serial or TCP/IP. We see both quite often. BacNET doesn’t usually provide for authentication or integrity validation, so once you get access to the BacNET, it’s game over for the building. And there are a variety of ways to get access to a building’s BacNET. The scenario shown in Mr. Robot is totally plausible, both in serial BacNET and via TCP,” says Rios.
The BACnet protocol defines a number of services used to communicate between building devices and also 59 object types that the services act on. But only in 2016 did the BACnet committee in charge of the protocol’s definition release an addendum adding IT security concepts. As of this writing it is still out for advisory public review.
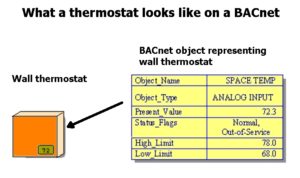
So a Pi attached to BACnet network lines would look like any other low-level node on the network. “Most control systems use a reference architecture where level five is your typical internet outside connection, level four is engineering operator consoles and traditional IT assets that communicate down to level three devices,” says Michael Chipley. “The level-three devices then communicate down to level-two devices. The Raspberry Pi is a level-two device. But there’s no authentication of the command line communication between any of these devices. BACnet is peer-to-peer protocol so it can have thousands of devices trusting each other on its network. As long as the command that’s issued is valid, the device will obey it. Same problem exists on proprietary networks.”
Out on the net
Once Elliot had done his dirty work with the Raspberry Pi, he was able to access the Steel Mountain BACnet from an ordinary laptop with an internet connection. Once again, experts say this scenario uses existing technology that’s widely available.
The website used in the show to see the Steel Mountain building automation network also exists in real life. It’s called Shodan (www.shodan.io) and is a search engine that lets users find not just HVAC systems but also routers, servers, and other equipment connected to the internet. Though designed for use by web security personnel, Shodan became notorious a few years ago when news sites noticed it could be used to access unprotected traffic lights and video baby monitors.
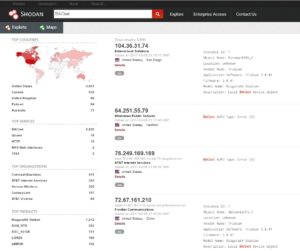
The way Shodan finds these unprotected devices is by crawling the internet rooking for IP addresses with open ports. The reason Shodan can find computer-controlled HVAC systems is that they’ve been plugged into a company web server that reaches the internet. (Conversely, Shodan won’t see HVAC systems operating on their own closed networks.) When Shodan notices a port left open without password protection, or with only the default password settings, it takes a snapshot of the connection and moves on.
As a quick review, ports are pieces of software generally used by transport layer protocols for identifying specific processes or types of network services. Specific port numbers are often used to identify specific services. Ports became necessary after computers became capable of executing multiple programs simultaneously and connected via packet-switched networks. Back when connections were strictly point-to-point and computers ran just one program at a time, there was no need for the concept of a port.
A port is always associated with an IP address of a host and the protocol used by the communication. A port is identified for each address and protocol by a 16-bit number, commonly called the port number. For example, an address might look like “protocol: TCP, IP address: 10.22.33.44, port number: 554”, which may be written 10.22.33.44:554 when the protocol is known from context.
In the previous example, the port number 554 is used by devices that employ real time streaming protocol. BACnet messages use the user datagram protocol port number 47808.
“Every day thousands more control systems show up on Shodan,” says Michael Chipley. “People don’t realize that when they have a misconfigured thermostat or HVAC controller, it is exposed. And technically, when you see an HVAC system on Shodan you haven’t hacked anything because the owner has posted the information for the whole world to see.”
Inside the network
Elliot Alderson and his cohorts used one other piece of software in their penetration of the Steel Mountain HVAC system. Called Kali Linux, it, too, is a real-world program. It is basically an operating system designed by two security experts for doing network penetration tests. It contains a toolkit for such tasks as cracking Wi-Fi passwords, creating fake networks, and analyzing network traffic. There are versions of it available for the Raspberry Pi. It is small enough to run from the Pi’s SD card.

In the case of the Mr. Robot hack, we might surmise that Kali was the means by which Elliot and his colleagues watched network traffic and determined which devices were the thermostats controlling the tape storage rooms. With that information, the Pi would have mimicked the thermostats and generated commands to the HVAC controller to boost the temperature in those rooms.
Given that the Mr. Robot episode was filmed a few years ago, you might wonder if a similar scheme would still work today. Odds are that it would, say the security experts.
“Network security for these devices hasn’t improved very much since 2014,” says Billy Rios. “The underlying BacNET protocol simply doesn’t have security built into it. That’s something that cannot easily be overcome by a single vendor or even a collection of vendors.”
“The vulnerabilities will be out there forever,” says Chipley. “You just have to assume systems are going to be exploited. So when they are compromised, you need to design them so they just fail gracefully. You have to adopt that approach because there is no way you are going to stop a determined aggressor from taking over. When we run simulated attacks, it is not a matter of if we are getting in the system, it is a matter of how fast. For real hackers, it is typically less than 30 minutes before they own everything.”
References
extremely minor correction: although Kali Linux is a “”tool” it is mainly a Linux distribution ( source: https://www.offensive-security.com/)