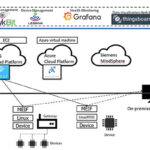
With the Internet of Things (IoT), industries are relying on connected devices that can interact with each other and also with processes and personnel thus helping businesses meet their goals efficiently. IoT enabled devices are being successfully used in multiple industries like manufacturing, construction, logistics, agriculture, etc. and helped to optimize assets, conserve resources and reduce expenses. Gartner estimates that 20 billion dedicated functional devices will be connected online by 2020.
While there are many benefits to be achieved from IoT, like anything else that is connected to the internet, IoT enabled devices are also vulnerable to security attacks. There have been several reports of hacking into IoT devices. Mirai botnet, which launched Distributed Denial of Service (DDoS) attack against Dyn servers disrupted the internet. According to The Guardian, the attack is considered to be the largest of its kind in history. Mirai botnet is primarily made up of IoT devices and which acted as malicious endpoints. Attackers attack devices that are vulnerable in nature. According to CNN, the FDA stated that specific Cardiac devices at St. Jude Medical are vulnerable and can be accessed by hackers in an unauthorized manner.
It is very clear from these examples that IoT ecosystems need to be secured. Due to the different implementations of IoT, the security requirements of each IoT ecosystem should be independently analyzed so proper security levels are implemented.
IoT security – available options
For a secure IoT ecosystem, IoT has to be secured at different levels like secure device, secure communications, and secure authorization and authentication techniques. There are various methods that can be used to implement security at each of these levels.
Device-level security involves verifying the authenticity and integrity of the device. The identity of each device can be protected by embedding security hardware. This security measure can protect the device against unauthorized data tampering and breach of information. Authentication through cryptography can protect IoT identity. The combination of hardware and secure cryptographic algorithms can protect the confidentiality of device identity. Also, chips that support the open standard Trusted Platform Module (TPM) can securely establish device identity, perform encryption algorithms and detect device anomalies and compromise.
Authentication level Security can be implemented by using Public Key Infrastructure (PKI) technology for secure authentication, encryption, key management, and digital signatures. PKI can also provide secure communication between the server and IoT devices. IoT can also achieve higher levels of security by integrating smart chips into the connected device. The smart chip can determine how the device should behave to protect information before and after a malicious attack. The embedded hardware can also secure access to the device.
Authorization level security ensures that there is no data leakage between two devices. Secure tokenization can add more layers of IoT security by protecting the confidentiality of information along with IoT privacy. Secure tokenization is the process of substituting sensitive data with a string of unique symbols that do not have a meaning. The unique symbols are known as security tokens that protect the confidentiality and privacy of information. Secure tokenization allows the creation of encrypted device ID number to keep the device ID hidden when transferred over the network. Tokenization improves IoT security.
An IoT device should integrate secure hardware component to support functions such as PKI and strong encryption algorithms. Smart cards can be used to login the user to the IoT server. The server authenticates the user, and a unique session key is generated that will enable the user to use the IoT device securely. Smart cards also help in encryption key management between the card, user and the device. This will ensure the confidentiality and integrity of the sensitive information being transmitted.
The need for securing IoT devices has also led to the manufacture of special chips called secure elements. A secure element is a microprocessor chip that can securely store sensitive information and run secure applications that supports sensitive information. They can store cryptographic keys and enhance memory security. They also offer a tamper-resistant environment for cryptographic data. Multiple secure elements with enhanced interface logic can be embedded in IoT devices. These secure elements are base controllers of smart cards.
Another method for securing the ecosystem is to add a hardware component that incorporates the Trusted Execution Environment (TEE) in the microprocessor. There is a need for the IoT device and the backend to communicate securely. Depending on the security component used in the device, the component can support encryption algorithms to all the device to securely connect to the IoT server (through a virtual private network for example). The secure component should secure store sensitive information about the server and its clients.
Conclusion
IoT implementation is not a new concept. It requires processing and storing of sensitive information and is gaining popularity with time. Businesses may be rushing to introduce IoT solutions without taking associated security risks into serious consideration. This leaves IoT devices vulnerable to various attacks. As a result, there is a need to secure IoT devices through secure designs and IoT life cycle management. Along with the secure implementation of IoT hardware and software, there is also a need for an international standard that will determine the minimum-security requirements for IoT devices.



Leave a Reply