By Rudy Ramos, Mouser Electronics
Most of us are familiar with the tricks used by malicious hackers to steal passwords or intercept private data. When we click a link, or start a chat, or send an email, it’s second nature to quickly check URLs and addresses to make sure that our data is going where we intended. However, sometimes, such caution is not enough, because even the standard routing protocols that link the internet and carry data around the world can be vulnerable to disruption. It is as if you board a flight to Honolulu and everything seems in order, but your plane lands in Pyongyang. One of the most alarming and pernicious Internet routing attacks is BGP (Border Gateway Protocol) hijacking.
BGP hijacking in simple terms means announcing to the entire internet: “Internet traffic sent to this numerical IP address range should be routed through my servers way over there because that is the best route.” The surprising result is that gigabytes of data actually will get routed via those servers on the way to its eventual destination, even though the new route is not the fastest—and perhaps does not even make sense because internet traffic between a company in New York and its bank in Boston, for example, is now traveling via Moscow.
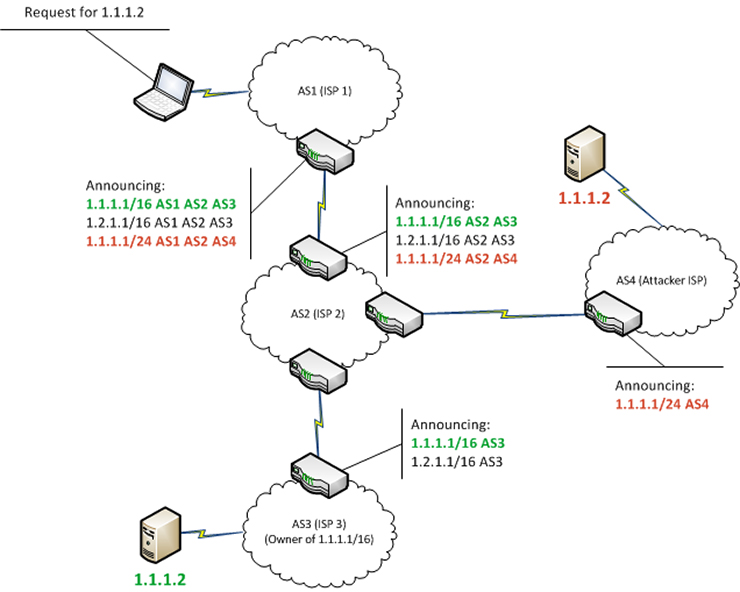
Routing attacks allow sensitive information (such as passwords, corporate secrets, banking information, or IoT data) to be copied, or altered, en route, unbeknownst to the sender or receiver or the data could be discarded—a denial of service attack. BGP’s surprising weakness is a legacy of the Internet’s origins as a network for universities and research institutes, which could all trust each other. What is more surprising is that security professionals have been stridently warning about this vulnerability for decades, yet it persists and increasingly being exploited. Internet governance bodies are working on solutions, but these are still apparently some years from being globally accepted.
Who can perform a BGP attack? Worldwide, there are more than 80,000 organizations, such as Internet Service Providers (ISPs), with authority to announce internet routes via BGP, and that number is increasing. A malicious actor could hack into one of those organizations, or even set up their own. Moreover, because BGP includes no formal identity verification, it’s also possible, in theory, to merely pretend to be one of these authorized organizations—a spoofing attack.
BGP incidents can impact billions and cost millions
Some well-known cases of BGP hijacking were simple configuration errors, though they still temporarily blocked internet connectivity for vast numbers of popular sites, from Amazon to Google to Facebook. For example, in 2008, officials in Pakistan were ordered to block local people from visiting YouTube, by re-routing Pakistani traffic destined for YouTube’s IP address ranges to a local address, where it was discarded. But due to a typing error, they failed to limit the routing change to their own country. Within minutes, they had blocked YouTube access for almost everyone in the world. In an even bigger blunder, in 2005, a Turkish ISP accidentally re-routed all Internet traffic in the world to themselves.
Both of these accidents caused business disruption and cost money. However, there have been cases in where BGP hijacking has been far harder to detect and where the intent was more suspect. What makes these cases both subtle and suspicious is that the re-routed data was not just dumped into a black hole, but was re-directed, potentially copied, and then immediately sent on to its intended recipient, leaving them none the wiser.
Recently, numerous incidents have seen data to financial, law enforcement and governmental websites unexpectedly taking detours through foreign countries far from their intended destination. In some cases, money has been stolen. Accusing fingers have been pointed at China, Russia, the US, and other nations. Sidestepping the question of blame, however, we can at least take some simple steps to mitigate the risks.
Simple steps to guarding against routing attacks
The most important defense against BGP hijacking, and also one of the easiest to implement, is to always use HTTPS (and other encryption protocols like SSL/TLS and SSH) for everything. Strict use of encryption does not prevent re-routing, but it does make our data far harder to read or alter en route.
Network administrators should enforce HTTPS Strict Transport Security (HSTS), to prevent connections falling back from HTTPS to insecure HTTP. Within organizations, we must ensure that users cannot defeat HTTPS by clicking through browser security alerts or accepting faked security certificates and unknown certificate authorities.
However, enforcement of HSTS requires user education, as well as the configuration of servers and clients. Note that older embedded hardware may struggle with encryption processing loads. For lower power consumption, particular in IoT devices, it would be ideal for silicon to handle these functions instead of by software.
Also, organizations can monitor the routes their internet data is taking and look out for suspicious routing changes. Remember to check routes in both directions, from client to server and vice-versa, because one direction could be normal while the other has been tampered with. There are several companies which provide such monitoring services.
To summarize the key lessons: Internet routing attacks are extremely dangerous, and currently, we cannot always prevent them, but with good systems design, end-to-end encryption, and user education, we can ensure that our data is encrypted and therefore of much less value to attackers.

Leave a Reply