Special instrumentation can help bullet-proof the communication equipment powering next-generation vehicles.
Craig Hendricks, Anritsu Co.
The roll-out of 5G is bringing a host of real-time Internet-of-Things (IoT) capabilities to automotive designs. Use cases such as enhanced Mobile Broadband (eMBB, high-data-rate use cases for 4G LTE and 5G NR services that allows a high data rate across a wide coverage area) and Ultra-Reliable Low Latency Communication (URLLC) are empowering autonomous vehicles, infotainment systems and security programs. They are also allowing automobiles to leverage smart cities systems (V2N). But these capabilities create a new set of design verification hurdles for engineers.
One requirement associated with emerging automotive designs utilizing 5G technologies is cybersecurity. Prevention of attacks that can create dangerous scenarios in automotive and other mission-critical applications is a new design consideration for engineers developing components and systems.
Much of this concern is due to vulnerabilities caused by the complex architecture associated with 5G. For example, instead of centralized hardware-based switching, 5G employs a software-defined network. This network employs virtualization functions that can be vulnerable from multiple points, if someone gains control of the software. Other vulnerabilities arise because of the high bandwidth and large number of devices connecting to the network.
Network slicing
The flexibility of the 5G architectural approach enables use of efficient, interoperable multi-service pipelines within the core network. These transmission paths support virtual end-to-end network services using a technique called network slicing. Network slicing allows multiple logical networks to run on top of a shared physical network infrastructure. The
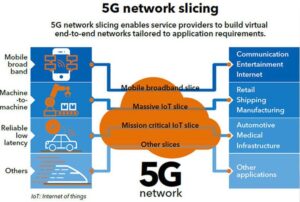
slices occupying a single physical network are separated such that traffic and security breaches from one slice cannot interfere with another slice. Each slice has the bandwidth and quality of service (QoS) parameters necessary to support a specific service class.
Network slicing supports advanced techniques such as URLLC and eMBB, as well as the traditional mobile voice and broadband services. It also brings benefits to telematics control units (TCUs) used in autonomous vehicles. And network slicing improves other Machine-to-Machine (M2M) connections used in infrastructure services for smart cities, smart grids, and smart roadways.
Though 5G networks benefit automotive designs, the trade-off is they introduce vulnerabilities at almost every layer of the network stack. Such security risks weren’t a concern with 4G LTE. But the air interface that connects 5G UE (user equipment) with base stations potentially let cyber criminals inject malicious control signals. These malicious signals can potentially misdirect traffic, take control of vehicles, force disconnections, or induce critical system failures.
There will be considerable 5G traffic offloaded from relatively secure carrier networks to the less secure internet. Recognizing the potential for nefarious activity, 5G network architectures integrate several security features, including security edge protection proxy at the border of the Public Land Mobile Network (PLMN, a mobile wireless network using earth-based stations rather than satellites), enhanced privacy for the Subscription Permanent Identifier (SUPI, a string of decimal digits representing the Mobile Country Code and Mobile Network Code identifying the network operator), and a unified authentication framework that includes the Security Anchor Function (SEAF decides whether UE is authentic via what’s called an anchor key). To design secure UE, engineers must use components, software, and design practices that ensure compatibility and compliance with ABBA (basically a parameter signifying which security features are enabled), SEAF, and other security mechanisms defined in 3GPP TS 33.501.
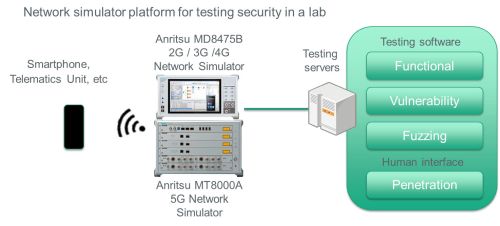
Also vital to protect automotive systems is testing to ensure the UE complies with 5G network security mechanisms. Engineers must have a high degree of confidence that their products can resist compromise or corruption. Many UE manufacturers employ a Practical Security Testing process to ensure product performance.
Practical Security Testing uses a network simulator such as a signaling tester or wireless communications test set. These tools serve as a base station to connect with the UE and a testing server that exercises the device using commercial or proprietary software. Functional security measurements are one of a series of tests necessary to verify the UE performs according to specification.
Similar to the general functional testing performed during design verification, testing for 5G automotive systems also focuses on security functions. Here, a network simulator typically exercises the UE with sequences created by a lab or a production server.
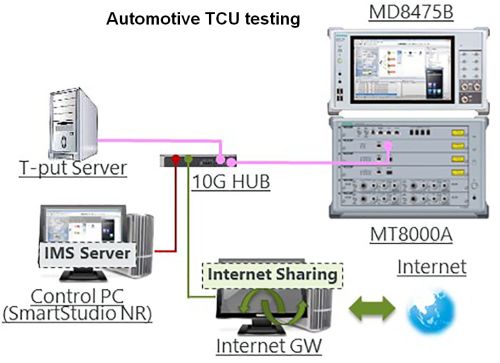
A powerful new generation of test and simulation equipment has been developed to address the specific security concerns associated with automotive designs. These systems can efficiently verify compliance with 3GPP by connecting with actual service servers. This lets comprehensive testing take place without the influence of an RF channel, as well as under specific network conditions. This approach can also reproduce bugs and cyber-attacks common in the field while the UE sits in the lab.
Efficient cyber-security testing requires flexible hardware with application-specific software. For example, mobility testing for E-UTRAN New Radio – Dual Connectivity (EN-DC is a way of enabling 5G services and data rates in a predominantly 4G network. UEs supporting EN-DC can connect simultaneously to LTE master nodes and 5G-NR secondary nodes.) Using this application-specific software, EN-DC mobility testing can take place without the need to create complicated scenarios. It simplifies the testing process while providing the flexibility for future tests as standards evolve.
Software is available to handle specific tests and levels of complexity. Dedicated software packages can let the base station emulator create an interactive test environment without complicated test scripts. They can support multi-system simulation of common actions such as, to name a few, cell selection/reselection, roaming, SRVCC (Single Radio Voice Call Continuity, a way of handing over VoLTE (Voice over LTE) to 2G/3G networks. VoLTE uses LTE channels for phone calls rather than low-bandwidth voice channels), and EPS fallback (lets phones use the 5G core with NR, but the radio access network may trigger moving the phone to an internet service during call establishment). Such a system makes it possible to efficiently create a real-world environment to test UE for key functions for IMS (IP Multimedia Core Network Subsystem, a framework for delivering IP multimedia services) such as VoLTE , VoNR (Voice over 5G NR), data communications, and messaging. All these tests can take place without forcing the operator to have an extensive understanding of the network protocol.
Script software is available that lets users create their own test cases. Engineers must have a deep knowledge of the protocol to write these low-level scripts. For example, users must write test scripts using a ladder sequence with an IMS protocol scripting option. The benefits of this more complex approach include a higher level of flexibility and scalability.
There is also software available to capture IMS call flows from a live network and a tool to convert that data into a script, removing the need for the deep knowledge of the IMS protocol. This approach also allows testing IMS functions using carrier-specific IMS implementations.
Script software also gives engineers the ability to:
- Check user-specific abnormal tests and protocol checks at any message level
- Conduct call processing of LTE for IMS development and evaluation
- Test STIR/SHAKEN (Secure Telephone Identity Revisited and Signature-based Handling of Asserted information using toKENs, a framework for ensuring the authenticity of a given call) to prevent VoIP call spoofing from spammers
- Have flexible support for evolving 5G core specification, such as Voice over NR (VoNR)
Dedicated software and network emulators verify the requirements of 5G use cases. For example, it’s more important to verify maximum throughput in eMBB on a 5G UE than on a 4G LTE device. Necessary tests include IP throughput performance and TCP/UDP/FTP. Tests must also support Carrier Aggregation (CA) with 2×2 or 4×4 multiple-input-multiple-output (MIMO) with up to 256QAM.
Engineers must also quantify power consumption and heat levels at maximum throughput to satisfy 3GPP standards. Software supports detailed settings related to the base station, packets communication state, UE Tx RF output, and power consumption.
Other functional tests for compliance include stress tests of the CPU and software at maximum throughput and tests of a device that supports dual SIM dual active (DSDA, where two SIM cards are constantly active). An example test would measure the UE as it simultaneously conducts 1,000 SMS messages, VoLTE, video streaming, and downloading a large file to measure how robust the software is and test for stack overflows.
Also critical for automotive designs is reject testing to see how a TCU responds in abnormal conditions and to duplicate field issues. There are three types of reject testing that can be preformed:
Cellular Signaling Message Reject – An example would be an attach reject with a specified reject cause code, and reject for a certain amount of time, a certain number of re-tries or on a certain cell.
IMS Message Reject – This is for testing abnormal situations with the IMS protocol to see how the TCU software responds.
APN Reject – For rejecting the connection when the TCU requests a certain APN name. (Access Point Name or APN is the name for the settings a phone reads to set up a connection to the gateway between the carrier’s cellular network and the public internet.)
All in all, new hardware and software help create economical test environments that emulate real-world scenarios to verify designs and ensure systems comply with 3GPP security standards.



Leave a Reply