By Chris Jones, Crypto Quantique
Digital health is the modern approach to healthcare, with the potential to broaden access and improve the quality and affordability of services. It’s how providers worldwide are expecting to deal with diverse pressures connected with factors such as population growth, increasing health awareness and demand for services, and the fact that more medical conditions can now be treated than ever before, even in an environment where budgets are constantly being squeezed.
However, digital health also exposes businesses to new risks associated with technology, data privacy, and compliance. On the one hand, digitization of patients’ medical records brings convenience and efficiency, and helps prevent clinical errors, but demands secure storage and cyber-protection of practitioners’ IT networks.
Cybersecurity challenges
Digital health is reliant on an increasing variety of smart, connected personal medical electronic devices for remotely monitoring and reporting patients’ vital signs, administering controlled quantities of medication, and maintaining critical functions such as cardiac pace-making. These devices are vulnerable to cyberattacks ranging from simple hacking and stealing passwords or sensitive medical data, to sabotage that can jeopardize treatment and threaten patients’ lives. The attacks could be ransomware exploits launched against high net-worth patients or healthcare providers, or malicious action aimed at specific individuals.
Keeping these digital devices secure is vital. However, for this aspect of digital health to work, the devices must remain easy for the patient to use independently without needing intensive technical support.
Establishing a Root-of-Trust (RoT) in the device itself is the first step in ensuring cybersecurity. Medical device makers need a convenient RoT that places minimal demand on the embedded processing resources, requires no understanding on the part of the user, yet is strong enough to resist attempts to take over or clone the device.
Protecting the root-of-trust
To connect a device securely to an application hosted on a server, its identity must be established beyond doubt. The identity must be unique, immutable – not changing over time, and unforgeable. In addition, data produced by the device must be impossible to read or corrupt if it is intercepted while in transit. Cryptography is central to achieving this and requires the device to be able to utilize cryptographic keys securely to prevent them from being discovered by an unauthorized party. Together, the device identity and cryptographic keys form the basis of the RoT (Figure 1).
This principle is widely adopted in new devices being developed to connect to the Internet of Things (IoT) and is equally applicable to medical devices to create the foundation for efficient and robust cyber-protection.
The conventional approach to establishing the RoT is to inject the unique identity and keys into the device’s main controller chip, typically a microcontroller (MCU) or application-specific IC (ASIC). The key injection is done at a trusted, third-party site during the device manufacturing process. This has two significant disadvantages. The process typically adds between $0.5 and $2 to the cost of the device risks of any security breaches that may happen at the third-party site.
An alternative approach avoids the cost and risks associated with injecting and storing sensitive information by taking advantage of Physically Unclonable Function (PUF) technology. A PUF derives the device’s identity from unique patterns in the silicon structure that result from the chip manufacturing process. Using these patterns, the chip generates its cryptographic keys on demand, so they are not saved permanently on the device. The identity and key generation are handled using IP integrated on the chip. The key generation IP is not security-sensitive as it is based on trusted algorithms that can be programmed using conventional equipment in a non-secure environment.
The first generation of PUF technology, which utilizes patterns in the silicon structure of the MCUs on-chip SRAM memory to generate the identity and keys. These PUFs are used in some MCUs and FPGAs from several semiconductor manufacturers including Microchip (Microsemi products), NXP, and Xilinx.
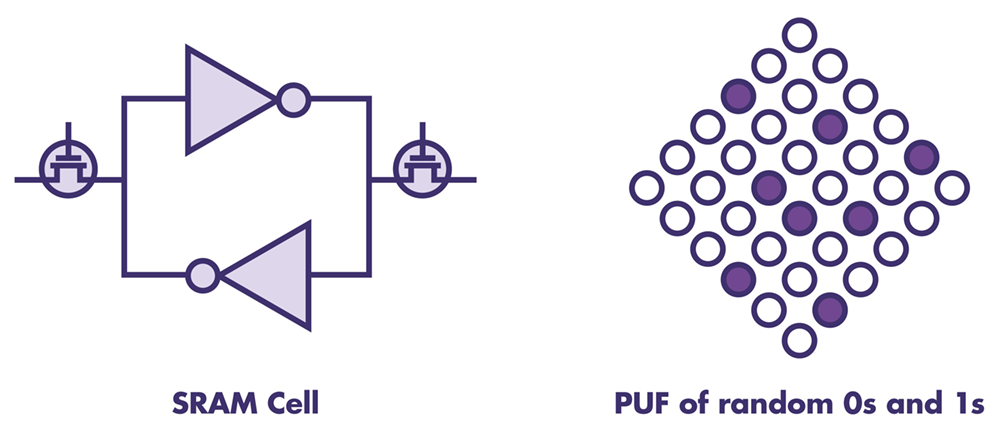
Second generation PUFs – stronger physically unclonable functions
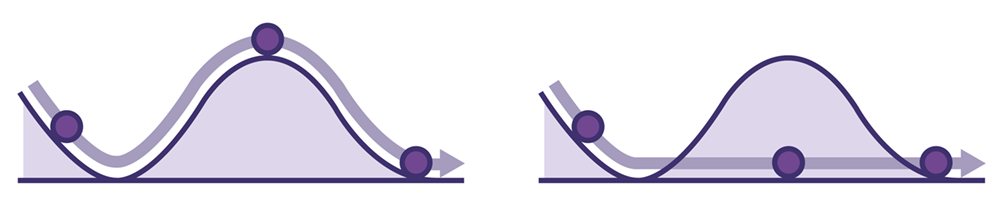
Second-generation PUFs leverage even more random phenomena within the chip to raise security to the next level. These take advantage of atomic-level differences and nano-structural imperfections that cause tiny variations in quantum tunneling currents. These quantum tunneling currents flow through the silicon oxide layer of standard CMOS transistors. These currents are in the order of femtoamps and display variations that are unique to the individual chip. The variations display a high degree of randomness which results in a unique identity of the host device. Also, multiple cryptographic keys, which have no mathematical correlation, can be generated by this technology. Both these factors enhance security. Also, compared with SRAM PUF, quantum tunneling technology eliminates the uncertainty inherent in SRAM startup states, minimizing the need for processor-intensive error correction and its negative impact on system power consumption.
Typically, the hardware IP needed to implement a quantum-tunneling PUF on-chip comprises a 64 x 64-bit cell array. It occupies a tiny silicon area, so minimizes additional cost, and can be implemented without changing the standard CMOS fabrication process, another cost-saving factor. Firmware injected into the IP block can generate up to eight 128-bit random numbers or ‘seeds’. One of these is designated as the enrolment seed and is used to generate a public and private pair of asymmetric cryptographic keys. A 256-bit cryptographic ‘hash’ is generated from the public key of this pair and used to register the MCU’s unique identity, usually on a cloud platform.
Semiconductor manufacturers will introduce MCUs with embedded second-generation PUFs during the next few months, providing medical device manufacturers with an opportunity to significantly improved device security.
Provisioning, onboarding, and lifetime management of medical devices
Whichever RoT technology is found in medical devices, network administrators need to provision, onboard, and manage them throughout their lifecycle. This can involve complex, time-consuming, multi-stage processes, particularly if devices are onboarded one at a time.
However, software applications are now available that enable automate these processes. Devices can be provisioned and onboarded in batches, enabling large numbers to be set up quickly and efficiently. Such applications check that each devices’ enrolment keys have been registered and then set up a secure TLS (Transport Layer Security) communication channel to exchange encrypted data with the devices.
Each device proves its identity through the TLS channel. The cloud application starts the process by sending a random number, or “challenge”. The device then encrypts the challenge using the private key generated within its RoT and returns the result. The returned information is then decrypted using the public key. If the device has ownership of the correct private “identity” key, then the decrypt reveals the original challenge, proving its identity. This onboarding process confirms the identity of each device and establishes a secure connection for exchanging data and credentials with applicable healthcare applications hosted in the cloud.
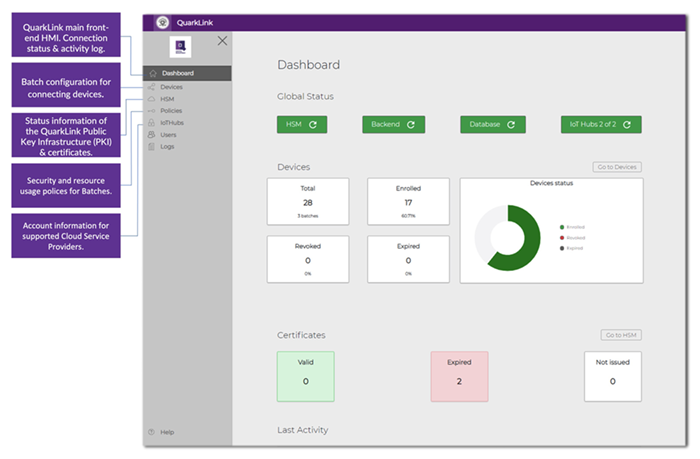
The secure cloud application also takes responsibility for lifetime device management, including handling device certificates and security policies, ensuring functional integrity, and dealing with firmware signing and encryption for secure over-the-air (OTA) updates. In addition, there are tools for renewing keys and certificates to help recovery after an interruption such as a system fault, as well as removing compromised devices from the network.
Conclusions
RoT technologies are seeing significant advances that improve the security of IoT devices, particularly where PUFs replace traditional key injection of identities and cryptographic keys.
Second-generation PUFs will soon provide superior protection for the medical devices’ RoTs by leveraging the high degree of randomness exhibited by quantum tunneling. This technology could help healthcare providers deliver more digital services to more patients, efficiently, cost-effectively, and safely.
Whichever RoT technology is deployed, new cloud-based automation platforms are now enabling secure and efficient provisioning, onboarding, and lifetime management of medical IoT devices at scale, without requiring network managers to have specialist cryptographic knowledge.
About the author
 Chris Jones is Crypto Quantique’s IoT Security Specialist. Following a 28-year career in project management and field applications engineering, Chris spent two years as a Senior Application Engineer at Secure ThingZ, Inc, in Cambridge, UK, working in IoT security. He joined Crypto Quantique in May 2020. Chris holds a BSc in Electrical and Electronic Engineering from the University of Coventry, UK.
Chris Jones is Crypto Quantique’s IoT Security Specialist. Following a 28-year career in project management and field applications engineering, Chris spent two years as a Senior Application Engineer at Secure ThingZ, Inc, in Cambridge, UK, working in IoT security. He joined Crypto Quantique in May 2020. Chris holds a BSc in Electrical and Electronic Engineering from the University of Coventry, UK.




Leave a Reply