The post-quantum cryptography (PQC) standardization program being run by the National Institute of Standards and Technology (NIST) is developing encryption algorithms to protect classical computers from attacks by quantum computers. NIST has announced the first four PQC algorithms and is preparing them for final development. In the meantime, organizations of all types are analyzing the potential impact the new security algorithms will have on their operations.
The end game for PQC begins next year when NIST starts developing mathematical tools and making them available so developers can integrate PQC algorithms into the global encryption infrastructure. The end game also consists of government and industry organizations like the National Security Agency (NSA) and the Financial Services Information Sharing and Analysis Center (FS-ISAC) developing detailed plans for PQC integration. But all that’s just the beginning of the post-quantum era when security protocols will be developed using quantum technologies instead of classical computing tools.
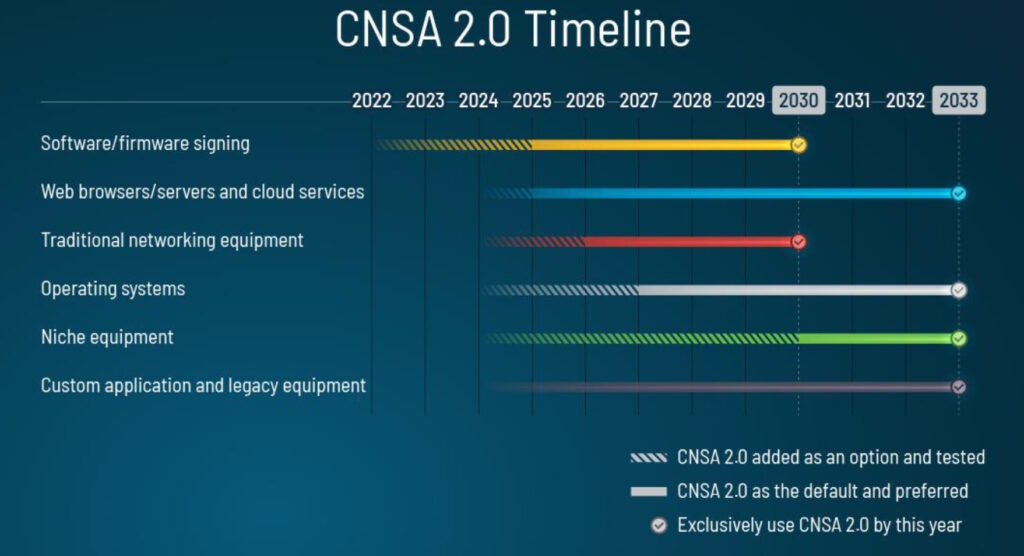
NSA anticipates the following timetable for implementing Commercial National Security Algorithm Suite 2.0 (CNSA 2.0) requirements for national security systems (Figure 1):
- Software and firmware signing to begin transitioning immediately and implemented as widely as possible by 2025 with exclusive use by 2030.
- Web browsers, servers, and cloud services are to be implemented in CNSA 2.0 by 2025, with exclusive use by 2033.
- Networking equipment like virtual private networks and routers prefer CNSA 2.0 by 2026 with exclusive use by 2030.
- Operating systems should adopt CNSA 2.0 as widely as possible by 2027, with exclusive use required by 2033.
- Niche equipment like large public-key infrastructure systems should support and prefer CNSA 2.0 by 2030 with exclusive use by 2033.
- Custom applications and legacy equipment updated to CNSA 2.0 or replaced by 2033.
Financial Services Information Sharing and Analysis Center
FS-ISAC breaks down security threats in a hierarchy beginning with Asymmetric Cryptography, which’s being addressed by the NIST efforts. Next are Cryptographic and security protocols that the Internet Engineering Task Force (IEFT) oversees, followed by Security protocols from the Organization for the Advancement of Structured Information Standards (OASIS). Symmetric cryptography and hash algorithms are at the bottom of the “threat stack” (Figure 2).
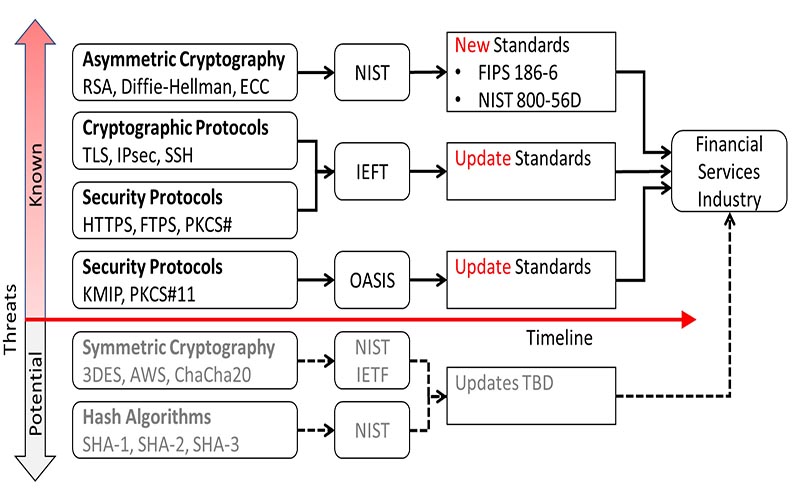
Symmetric cryptography and hash algorithms are future concerns of the FS-ISAC but are below the red timeline since they are currently not in the scope of the NIST PQC program. FS-ISAC has security concerns beyond the scope of the NIST activities, like the ANSI standard X9.24-2 that defines Remote Key Load (RKL) for use with automatic teller machines and point-of-sale terminals. RSA is used for key transport and digital signature to install the ATM symmetric keys: the PIN encryption key (PEK) and the key-encryption key (KEK). Many applications use transparent data encryption for database encryption, and some systems use RSA to manage the symmetric KEK for the symmetric database encryption keys. So, while the NIST activities are important, they are not all-encompassing.
Quantum leap in security
When quantum technologies are applied, security can move to a much higher level. Examples of quantum security technologies include quantum key distribution (QKD) and quantum random number generation (QRNG).
Using quantum communication, QKD enables the direct sharing of secure keys without the possibility of undetected tampering or eavesdropping. Quantum communications are inherently tamper-proof, and any attempt to disrupt or observe the communications leaves easily identified physical traces. QRNG will provide a physically and provably secure source of randomness due to the physics and mechanics of quantum processes resulting in inherently secure algorithms.
Summary
The development and deployment of PQCs may be the end game for the NIST post-quantum cryptography program, but it’s only the beginning of a new era in security. Security will move to a higher level when quantum security technologies are developed.
References
Announcing the Commercial National Security Algorithm Suite 2.0, National Security Agency
Cryptography in a Post-Quantum World, Accenture
Post-Quantum Cryptography (PQC) Working Group, Financial Services Information Sharing and Analysis Center