Ensuring automotive processors can’t be hacked
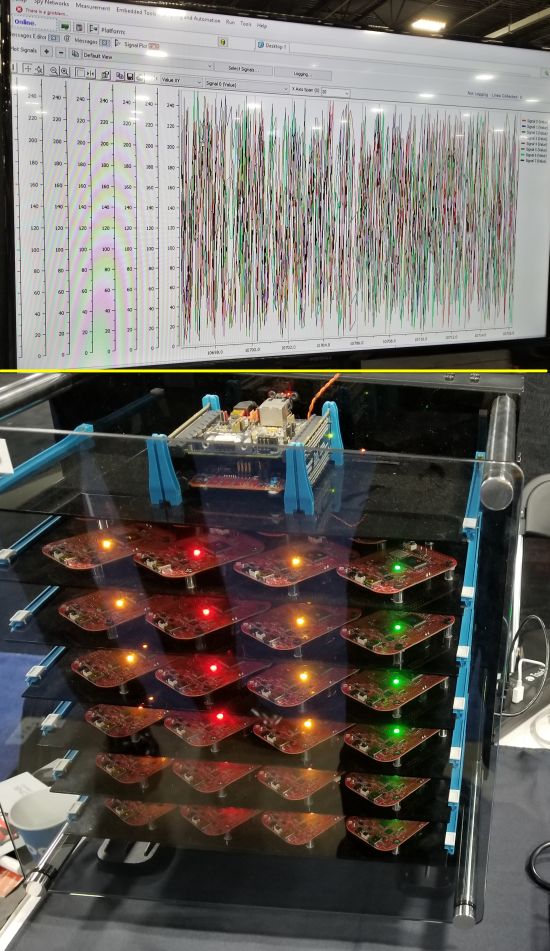 What you are looking at in the bottom image is the BrainBox by Trillium Secure Inc. It is basically a test platform for security and penetration testing. The small PCBs visible in the BrainBox all contain low-level automotive engine control units, up to 150 of them. Trillium produces software-based security tech that is compact enough to run on the resource-constrained ECUs you see in the BrainBox. The top display is of CANbus bytes after they have been scrambled by one of Trillium’s encryption algorithms. Trillium says its software is agnostic in terms of hardware and operating system. One of Trillium’s security tricks is to create a master key using a public key (asymmetric) cryptographic key establishment algorithm. The message payloads communicated between ECUs on the in-vehicle network get encrypted using a proprietary symmetric session key management system. A combination of CAN ID Hopping and Unique Device ID (UID) is applied to each message payload. Authentication doesn’t used HMAC (keyed-hash message authentication code), having the advantage of not consuming a byte of payload for the HMAC. Another portion of the Trillium security system is called SecureIXS, a platform based on in-house developed machine learning algorithms that combines intrusion detection, intrusion protection and other smart firewall functions.
What you are looking at in the bottom image is the BrainBox by Trillium Secure Inc. It is basically a test platform for security and penetration testing. The small PCBs visible in the BrainBox all contain low-level automotive engine control units, up to 150 of them. Trillium produces software-based security tech that is compact enough to run on the resource-constrained ECUs you see in the BrainBox. The top display is of CANbus bytes after they have been scrambled by one of Trillium’s encryption algorithms. Trillium says its software is agnostic in terms of hardware and operating system. One of Trillium’s security tricks is to create a master key using a public key (asymmetric) cryptographic key establishment algorithm. The message payloads communicated between ECUs on the in-vehicle network get encrypted using a proprietary symmetric session key management system. A combination of CAN ID Hopping and Unique Device ID (UID) is applied to each message payload. Authentication doesn’t used HMAC (keyed-hash message authentication code), having the advantage of not consuming a byte of payload for the HMAC. Another portion of the Trillium security system is called SecureIXS, a platform based on in-house developed machine learning algorithms that combines intrusion detection, intrusion protection and other smart firewall functions.
NEXT PAGE: The 2018 Luxury green car of the year






Leave a Reply