By Rob Oshana, Vice President Software Engineering, Research and Development, Edge Processing at NXP Semiconductors
In today’s connected world, a growing number of applications depend on embedded devices, collecting and acting upon data from a wide range of physical processes. As the computing power of the Systems-on-Chip (SoC) at the heart of these devices continues to grow, more decision-making is devolved from the cloud to the edge, turning this rapidly increasing number of edge devices into attractive targets for attackers.
The vulnerability of the IoT is, therefore, a growing concern. Data transmitted to the cloud needs protection, and commands received from remote services need validation. Additionally, while services deployed in the cloud benefit from high-security data center infrastructure, edge devices are installed in many different locations, where physical protection methods can be limited.
Security is, therefore, a fundamental property of the edge device, and developers must design-in security from the outset. The fundamental network security concepts of data in transit, data at rest, and access control mechanisms apply equally to the security of edge devices. However, additional protection measures and a level of intrusion detection capability are required because of their physical locations. These requirements must be built into MCU designs by hardware capabilities such as root of trust, (RoT), tamper detection, secure boot, and secure enclaves coupled with advanced software mitigation techniques.
Security for edge devices is two-fold
Both functional and platform security primitives are deployed in the security of edge devices. Functional security measures keep sensitive data secure and private, for example, by encrypting messages passed between two edge devices. Platform security primitives protect the implementation of functional security measures from remote or local attackers. The protection of the secret key used to encrypt and decrypt the messages passing between edge devices is an example of platform security.
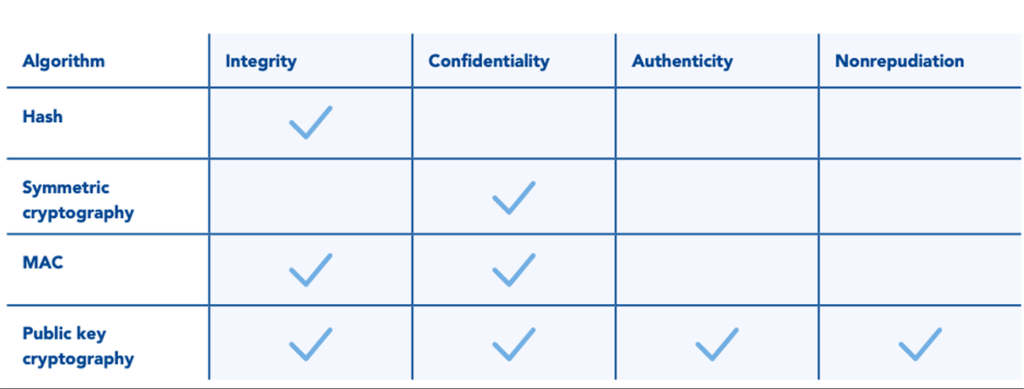
Both types of security measures employ cryptographic features to provide one or more of the following capabilities in a system:
- Integrity – the data received is identical to the data sent
- Confidentiality – A third party cannot understand the message being communicated
- Authenticity – The authenticity of the message can be verified by the recipient
- Nonrepudiation – the sender cannot deny having sent the message
Cryptographic features and key management techniques enable the protection of in-transit and at-rest data, ensuring that the edge booting device is running authentic, authorized firmware and software. A unique identity can also be created for the edge device, enabling a corrupt device to be identified and isolated.
The most commonly used cryptographic features and their applications are illustrated in Table 1.
Security implementation techniques
Advanced security measures require significant processing capabilities, and SoC developers employ various hardware and software techniques to optimize chip performance while managing power consumption.
Microprocessor units, (MPUs), with hardware acceleration, and hardware random number generation capabilities, fig 1, offload the computational overheads of the security features, either to an extension of the main processor or to a purpose-built co-processor or core. NXP’s i.MX product family, for example, includes specific hardware for cryptographic computation acceleration – the Cryptographic Accelerator and Assurance Module (CAAM). The CAAM also offers a unique key-wrapping mechanism protecting sensitive keys from being exposed to attackers.
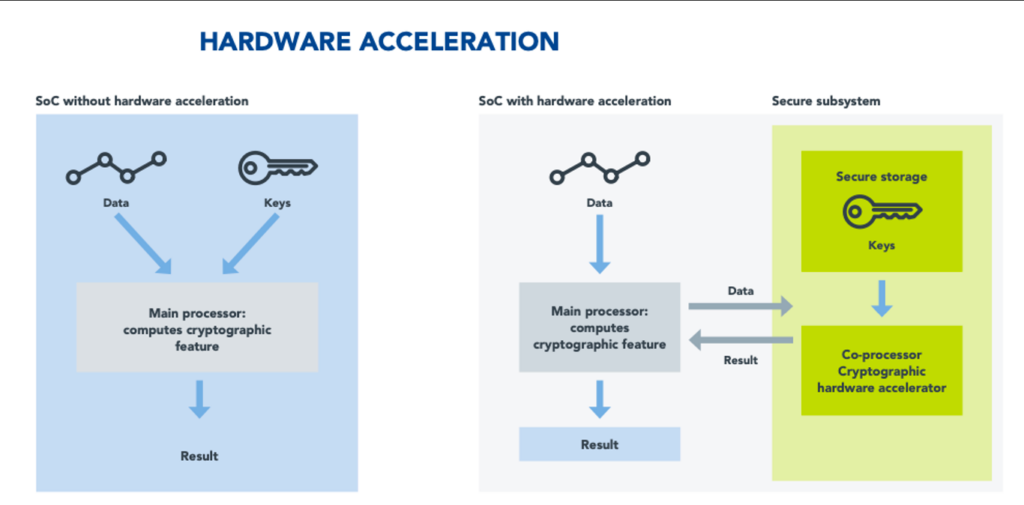
As separate processors within the MPU, hardware accelerators are also effective isolation devices. The isolation of storage and processing of sensitive information is a common secure mitigation technique, and multicore MPUs offer effective isolation capabilities. With its own processing unit and local memory, the accelerator’s resources cannot be accessed by the other cores in the MPU, providing isolation capabilities to the system while not compromising the overall system performance.
The architectures of many modern edge devices enable the implementation of public key infrastructures, (PKI), for edge computing. A third party certifies the binding between public keys, entities, individuals, and/or organizations using a digital certificate in a PKI. The security features of the more advanced SoCs found in edge devices enable them to act as the third party in a PKI.
Other key security implementation techniques used in edge devices include:
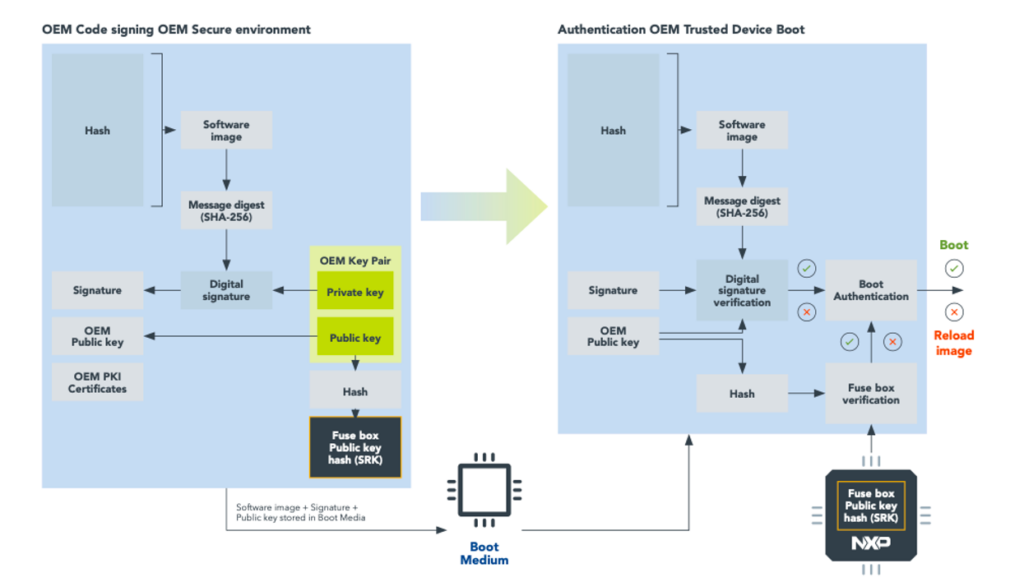
Secure Boot: Chain of Trust
A secure boot implementation guarantees that genuine, trusted binaries run on the system by starting from an immutable memory within the SoC. The immutable part of the SoC and its features are also referred to as a root of trust, (RoT), and specialized hardware security modules (HSMs) are often used to manage and protect the private key associated with RoT. An example of a secure boot implementation can be seen in many of the NXP i.MX range of applications processors which use a mechanism called high assurance boot (HAB), figure 2.
Trusted Execution Environment
A trusted execution environment (TEE) is a safe zone within an application processor, enabling separate execution of safe, trusted software from software with vulnerabilities such as large operating systems. Hardware vendors support TEE by including hardware extensions in their MPU designs, with examples including Intel SGX9, AMD Secure Encryption Virtualization (SEV)10, and Arm® TrustZone®11.
Virtualization
Virtualization clusters the applications performed by the edge device into virtual machines, (VMs), executed by a hypervisor that also manages resource sharing among the virtual machines. If an attack compromises a VM, the other VMs will be unaffected, assuming that the hypervisor is not affected. There are several methods of implementing virtualization, including using a XEN hypervisor or a “docker” implementation. Additionally, modern SoCs provide hardware support for virtualization, the most common being memory management, which ensures secure memory partitioning.
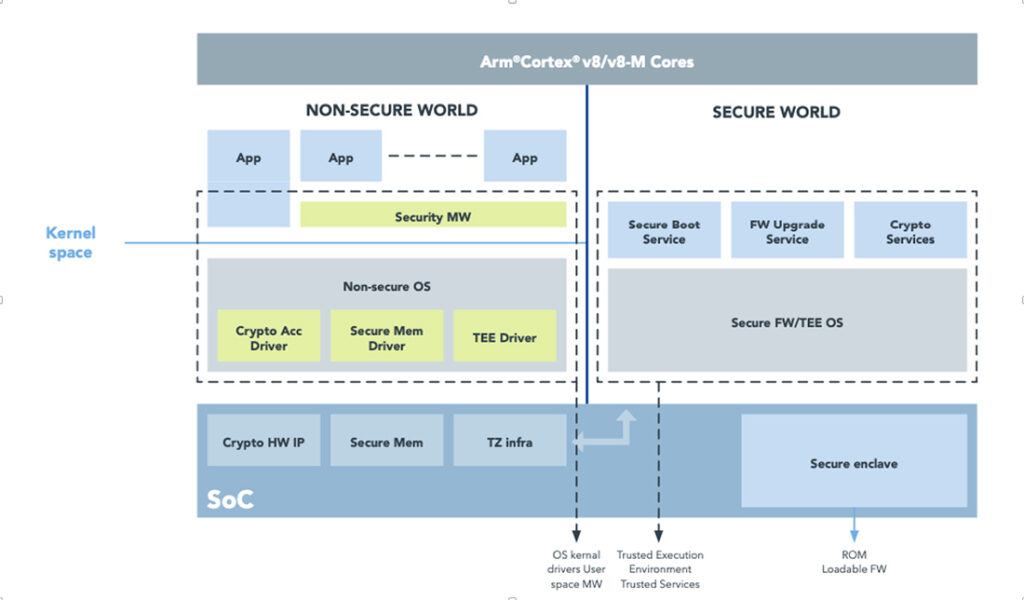
The role of software
Software architectures unlock the power of hardware in the implementation of security measures. Figure 3 shows an example of an edge device software stack that uses Arm TrustZone to provide two execution environments. The non-secure environment runs the rich Linux OS, while the secure environment runs the open, portable OP-TEE software. Trusted applications in the open software offer cryptographic features to the Linux OS by using API access to core functionalities such as cryptographic, key, and storage operations. Those functions can be accelerated in hardware, for example, using the CAAM hardware on NXP i.MX devices.
Security should not be an afterthought
Security must be considered from Day 0 of an edge device’s development. Although the correct implementation of security is a complex and challenging task, the sooner it is addressed, the higher the chances that the end device will be fit for purpose – at a cost that does not threaten the project viability.
About the author
 Robert Oshana is Vice President of Software Engineering R&D for the Edge Processing business line at NXP Semiconductors. He serves on multiple industry advisory boards and is a recognized international speaker. He is chief editor of Essentials of Edge Computing (2022), and has published numerous other books and articles on software engineering and embedded systems. He is also an adjunct professor at Southern Methodist University and is a Senior Member of IEEE.
Robert Oshana is Vice President of Software Engineering R&D for the Edge Processing business line at NXP Semiconductors. He serves on multiple industry advisory boards and is a recognized international speaker. He is chief editor of Essentials of Edge Computing (2022), and has published numerous other books and articles on software engineering and embedded systems. He is also an adjunct professor at Southern Methodist University and is a Senior Member of IEEE.

Leave a Reply