By Rebecca Reinkunz, Release Manager, Hyperstone
NAND flash memory is used in various consumer and industrial products, from laptops and mobile phones to industrial robotics, medical equipment, and embedded IoT devices, such as sensors and controllers. In our increasingly connected world, adequate and robust security measures are required at all vulnerable points in these applications, including the data storage system. When choosing or designing a NAND flash storage system, it is therefore essential to ensure that the memory’s security meets the application’s requirements.
Implementing modern security techniques requires the availability of sufficient processing capabilities. As the “brain” of the storage system, it is therefore essential that the NAND flash memory and controller are powerful enough to support the level of security required by the overall storage system. This article gives an overview of NAND flash security, covering the most common hardware and software techniques, helping to inform the reader when a choice of NAND controller must be made.
Digital data protection
The overall security goals of any IT system—Confidentiality, Integrity, and Source Authenticity—are equally relevant to digital storage solutions:
- Integrity – ensures that the data received is identical to the data sent
- Confidentiality – ensures that a third party cannot understand the data being communicated
- Authenticity – ensures that the recipient of the message can verify the identity of the source
These security goals apply across the full lifecycle of the stored data, which can be subdivided into three separate states. When moving between the storage device and the data source (user, sensor, etc.), the state is known as Data in Transit. When the transmission takes place over an untrusted channel—as is increasingly the case with wireless connectivity—security measures must ensure that the data is not modified between the source and destination.
The controller of a storage system performs various operations on the data, including processing I/O requests from the host, data encryption and decryption, ECC (error correction code) encoding, wear leveling, and garbage collection. These operations occur during the Data in Operation state, and the security system must prevent any unauthorized access to the data.
The principal function of the digital storage system is to maintain the integrity of the Data in Storage. During this state, access by unauthorized parties must be prevented without impacting the legitimate activities of authorized parties.
Several well-established security techniques have been developed over the years, broadly categorized into functional and platform measures. Functional security measures use cryptography techniques to protect sensitive data while platform security primitives protect the implementation of functional security measures from attackers. Ensuring both security measures requires a powerful computing resource, which the flash memory controller provides.
Common security techniques
Cryptography is based on mathematical abstractions. Modern security techniques use cryptographic algorithms as basic building blocks, combining cryptographic primitives to ensure confidentiality, integrity, and source authentication of the protected data. Four main types of cryptography are employed in NAND storage security solutions:
- The Cryptographic hash function maps any amount of input data to a fixed number of output bits. It has three main properties.
- Uniqueness, in that the input data must lead to the same output bits.
- Reversibility, in that, while output data can be easily generated from the known input, it is computationally infeasible to retrieve the input data from the generated output.
- And Collison resistance in that it is computationally infeasible for two different input data points to map to the same output result.

Several hash functions are available; several are standardized, coming from the SHA-2 family, including SHA-256, which maps the input bit string to a 256-bit output value.
- Symmetric key algorithms use a secret key shared by both sender, and receiver, to encrypt and decrypt data. These algorithms support relatively fast operations, so are preferred when significant amounts of data they must be exchanged. The Advanced Encryption Standard (AES) is a highly robust symmetric key algorithm, of which the AES6 family (AES-128, AES-192, AES-256) is the most used. Providing 128-bit block encryption, the AES6 family supports 128, 192, and 256-bit key sizes. Several modes of operation are available, including CBC— mainly used for encrypting data in transit, and XTS— intended for encrypting data on a block-structured storage device (data in storage).
- In public key or asymmetric key cryptography, a key pair is used by each participant in the transaction. The key pair comprises a private key (known only by the key pair’s owner) and a public key (known by all participants.) The two keys are different but mathematically related, and it is computationally infeasible to derive the private key from the public key. Asymmetric key algorithms are used for both confidentiality, where the public key is used for encryption, and authentication, where the private key is used. One example of a public-key cryptosystem is RSA, which provides a high level of confidentiality and is used for encrypted communications carrying sensitive data such as passwords and symmetric keys.
- To ensure a high level of security, the basis for cryptography and symmetric as well as asymmetric encryption are keys that are derived from random numbers. These are mainly generated by random number generators (RNG) which create a series of numbers that can only be predicted by random chance. There are two types of RNGs, true random number generators (TRNG), which generate completely random number sequences, and cryptographically secure pseudo-random number generators (PRNG). These PRNGs require initial seed values which must be random and are generated by true, random number generators (TRNGs) or entropy sources. A TRNG is implemented by sampling and processing raw data from a physical noise source, such as a free-running ring oscillator.
Advanced security measures such as cryptographic algorithms require significant processing capabilities, placing specific requirements on the NAND flash controller, the “brains” behind the storage system.
Implementation of digital security within the controller
As well as providing the compute resources to support the cryptographic algorithms, the architecture of the controller must be capable of supporting the platform security primitives required to protect the functional security measures. Many modern SoCs integrate platform security capabilities or the most common are:
- Secure boot loads from an immutable memory within the SoC, ensuring that trusted binaries are running on the system. As well as immutable memory, components of a secure boot include software authentication, a trusted boot loader, and a dedicated secure processor.
- Regular firmware updates are essential to the operation of any system and secure and reliable remote provisioning mechanisms ensure the authenticity and validity of firmware updates.
- Memory isolation defines a secure area of system memory, reserved for dedicated code and inaccessible y other system software.
- One-time programmable (OTP) memory is non-volatile memory where each bit is implemented as an eFuse. eFuses can be factory or user programmed but cannot be changed more than once after manufacturing. OTP memory stores system configuration information required at boot time, including system personalization strings and firmware versioning.
- Unique identity is a common security technique that underpins the root-of-trust concept. A device with a unique, secret identity enables authentication, key generation, key exchange, and more advanced cryptographic applications. Unique IDs can be embedded in a device using solutions such as non-volatile memories or Physical Unclonable Functions (PUFs). Recently introduced PUFs are more complex to implement but provide stronger physical security, and SRAM-based PUFs are increasingly adopted in commercial products.
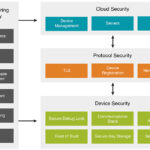
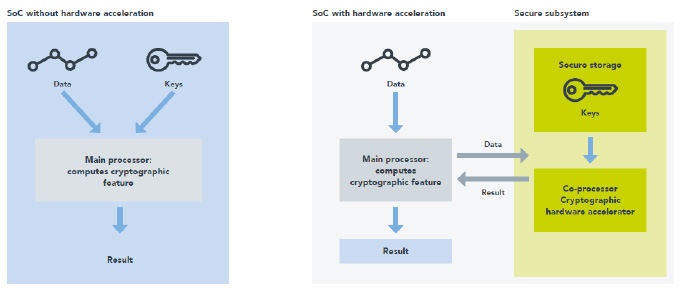
- Modern SoC developers are integrating various hardware and software techniques to optimize chip performance and power consumption while supporting advanced security techniques (figure 2). Features include multiple cores within the Microprocessor Unit (MPU), and separate Hardware Security Modules (HSMs), to which the security functions can be devolved. Both options support the isolation of security functionality and other features, including hardware accelerators to support cryptographic algorithms.
Security standardization
Industry standards ensure interoperability between the various security and cryptographic algorithms. These standards, specifications, and guidelines for data security are essential to enable manufacturers to develop more robust security-aware products. The National Institute of Standards and Technology (NIST) and the Trusted Computing Group (TCG) are two key industry bodies engaged in developing standards, recommendations, and various security hardware and software components.
Conclusion
Our society relies increasingly on connectivity to function, and each connected device offers a potential attack surface to the malicious attacker. Digital security measures have evolved considerably as connectivity has become more ubiquitous, and developers must ensure that the security of their devices meets the application’s requirements. NAND flash memory is used in more and more connected devices, and the memory controller is key to the overall security of the storage system. It is, therefore, important to understand the security capabilities of the controller when choosing or designing a NAND flash memory system.
About the author
 Rebecca Reinkunz is a Release Manager at Hyperstone, a leading developer of embedded flash controllers. Rebecca plans, organizes, and oversees firmware releases from request through the entire development process to the actual release. Her interest in future technologies is currently leading her to become more involved in security issues in order to build up a broad expertise for the company in this area. Before joining Hyperstone, she completed her master’s degree in industrial engineering with a focus on electrical engineering and information technology at the HTWG Konstanz.
Rebecca Reinkunz is a Release Manager at Hyperstone, a leading developer of embedded flash controllers. Rebecca plans, organizes, and oversees firmware releases from request through the entire development process to the actual release. Her interest in future technologies is currently leading her to become more involved in security issues in order to build up a broad expertise for the company in this area. Before joining Hyperstone, she completed her master’s degree in industrial engineering with a focus on electrical engineering and information technology at the HTWG Konstanz.