One of the hottest tech trends is artificial intelligence (AI) and its applications. Various sectors are using AI to solve problems and gain productivity. For instance, a school recently deployed a virtual telephone assistant, also known as a conversational agent, to help students with questions on what classes to take. Students were happy with the […]
LoRaWAN security design tips, Part 2: Taking the integrated approach
Part 1 of this two-part series on security design discussed using a stand-alone security chip. Here in Part 2, we’ll cover solutions that use an integrated chip and module, combining security and microcontroller (MCU) functions in a single chip. Integrated chip Cypress’ PSoC 6 MCU single-chip, dual-core architecture comprises the Arm Cortex-M4 and the Arm […]
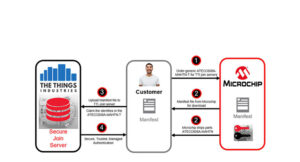
LoRaWAN security design tips: Designing with a stand-alone security chip
With the growth of the Internet of Things, cyber attacks are increasing at an alarming rate (Figure 1). Key provisioning, a process of key generation and device authentication, is a critical part of establishing security. Whoever holds the key will be able to access the payloads, i.e. the valuable data stored in the application server(s). […]
Cybersecurity basics: Authentication and “key” management in LoRaWAN, Part 2
In part 1, we described the process of providing end-to-end security and some of the challenges in achieving network security. In this installment, we will go over how authentication work to achieve end-to-end network security between the end devices and the application servers. Device authentication and key management Each LoRaWAN device is given a unique 128-bit […]
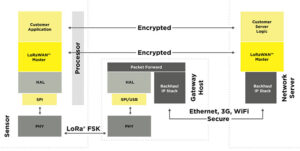
Cybersecurity basics: Server and end device relationship to LoRaWAN network, Part 1
Providing end-to-end security is the ultimate security goal of every wireless network. Each reported successful cyber attack serves as a reminder that achieving security is easier said than done. Let’s first examine the process. Most of us know about using strong passwords and encryption. The most vulnerable security component is key management during device activation […]