Zero trust architectures (ZTAs) are a reaction to the emergence of cloud computing, remote work, and bringing your own device (BYOD) into enterprise networks. Those trends result in networks not completely contained within an enterprise-owned boundary, significantly complicating network security needs. This article briefly reviews the purpose and structure of ZTAs, looks at some relevant […]
What can be done to prepare for post quantum cryptography?
Post-quantum cryptography (PQC), also called quantum-safe cryptography, uses mathematical algorithms to create security environments resistant to quantum computer attacks. PQC is a rapidly evolving technology, and preparing for its adoption requires keeping up with developments in several areas. As part of the formalization of PQC algorithms, NIST has finalized the algorithms and changed their names […]
What’s new in the NIST CSF 2.0 framework?
The NIST Cybersecurity Framework (CSF) 2.0 is the first major update since its creation in 2014. It was finalized in early 2024. This article reviews some of the important changes in CSF 2.0 compared with v1.1, briefly examines how v2.0 improves alignment with other cybersecurity standards and frameworks and compares CSF 2.0 with the ISO […]
What are the elements of secure boot processes?
The secure boot protects devices from unauthorized modification by verifying the authenticity of the boot code. Its importance is growing as society digitalizes and the number of devices on the Internet of Things (IoT) soars. A secure boot prevents an adversary from compromising device operation. This article reviews the basic elements of secure boot processes, […]
How are AI and ML used for advanced threat detection?
The increasing number of threat vectors and the growing size of the attack surface in today’s communication and computer networks demand more powerful and faster threat detection. Legacy tools are no longer adequate. To ensure cybersecurity, high-speed threat detection based on artificial intelligence (AI) and machine learning (ML) is increasingly being deployed. This article reviews […]
How is Zephyr used for edge AI and sensors?
Zephyr is a scalable open-source real-time operating system (RTOS) hosted by the Internet of Things (IoT) and embedded technology section of the Linux Foundation. Its modular architecture makes it highly flexible and suitable for resource-constrained edge devices and sensors. This article reviews Zephyr’s structure and features, examines how Zephyr supports neural networks, and discusses how […]
How do AI and ML enhance SASE security?
Secure Access Service Edge (SASE) has emerged as a leading architecture for cloud deployments. Its primary function is to provide comprehensive cloud-based secure access while maintaining seamless access to data and applications for users of cloud computing services. This article compares SASE with a traditional network architecture and then looks at how artificial intelligence (AI) […]
How is HIL testing used for onboard EV chargers?
Hardware-in-the-loop (HIL) testing is a real-time simulation that enables designers to test embedded code for EV chargers without needing the actual system hardware. It speeds development efforts and reduces development costs. This article begins with an overview of HIL testing and onboard chargers (OBCs), looks at specific types of HIL testing applied to OBCs, and […]
How does a recurrent neural network (RNN) remember?
There are several types of neural networks (NNs). Recurrent NNs (RNNs) can “remember” data and use past information for inferences. This article compares recurrent NNs with feed-forward NNs (FFNNs) that can’t remember, then digs into the concept of backpropagation through time (BPTT) and closes by looking at long short-term memory (LSTM) RNNs. RNNs and FFNNs […]
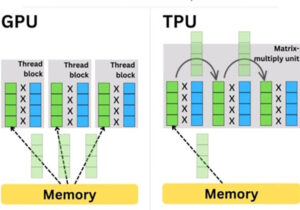
What’s the difference between GPUs and TPUs for AI processing?
Graphic processing units (GPUs) and tensor processing units (TPUs) are specialized ICs that support different types of artificial intelligence (AI) and machine learning (ML) algorithms. This article begins with a brief overview of tensors and where they fit into the mathematics of AI and ML; it then looks at the different structures of GPUs and […]