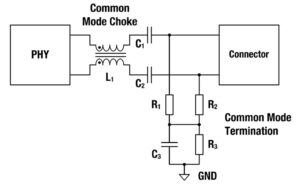
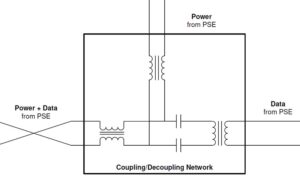
Common mode inductors (CMIs) are important components in all Single-Pair Ethernet (SPE) designs and are part of the coupling and decoupling network (CDN) that connects the SPE electronics to the network cabling. This FAQ begins with a brief review of the operation of CMIs and then looks at how the CDN fits into SPE designs […]
How to specify differential mode inductors for Single-Pair Ethernet?
Differential mode inductors (DMIs) are important components for Power over Data Line (PoDL) and the related Single Pair power over Ethernet (SPoE) standards. This FAQ begins with a review of where DMIs fit into Single-Pair Ethernet (SPE), then compares PoDL and SPoE implementations and application targets. Coupling and decoupling DMIs play an important role in […]
What is Single-Pair Ethernet and PoDL?
Single-Pair Ethernet (SPE) is defined in IEEE 802.3 and adapts the basic Ethernet standard to use a single wire pair. Power over data line (PoDL) is sometimes referred to as power over Ethernet (PoE) adapted for SPE. That’s only partially correct, PoDL is optimized specifically for use in automotive and similar environments, and the newer […]
How do MCUs support automotive infotainment systems?
In vehicle infotainment (IVI) systems are increasingly important and complex. What’s needed from a microcontroller (MCU) in an IVI? A lot, but exactly what depends on the sophistication and mix of info and ‘tainment. Multiple cores are often needed, and so are hardware accelerators for compute-intensive functions. Considerations include connectivity, human-machine interfaces (HMIs) beyond simple […]
How do the seven types of V2X connectivity work?
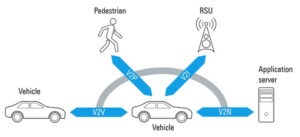
Vehicle-to-everything (V2X) communication includes vehicle-to-network (V2N), vehicle-to-infrastructure (V2I), vehicle-to-vehicle (V2V), vehicle-to-cloud (V2C), vehicle-to-pedestrian (V2P), vehicle to device (V2D), and vehicle to grid (V2G). This FAQ begins with a review of dedicated short-range communication (DSRC) and cellular vehicle-to-everything (C-V2X) technologies for V2X communications, looks at the four V2X service types and the structure of telematics control […]
What are the five levels of vehicle connectivity?
There are several efforts underway to define levels of vehicle connectivity that parallel the levels of driving automation defined by the Society of Automotive Engineers (SAE). The concept of autonomous vehicles, particularly at the higher levels of automation like self-driving cars, is still largely aspirational and a goal for some time in the future. Connectivity, […]
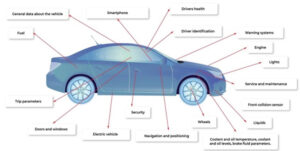
What’s different about MCUs for use in vehicle networking?
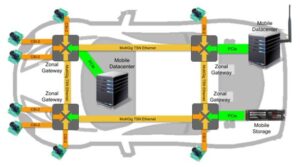
The increasing use of automated driving functions, more sensors and actuators, and growing V2X connectivity is increasing the challenges related to vehicle electric/electronic (E/E) architectures and in-vehicle networking (IVN). This FAQ will review the performance requirements for microcontrollers (MCUs) needed to support time-sensitive networking (TSN) in IVNs, move over to look at service-oriented gateways, domain […]
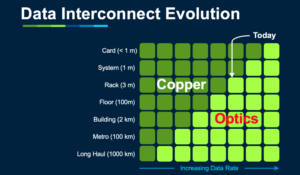
What embedded protocols can you use for optical connectivity?
Communication protocols and protocol stacks like peripheral component interconnect express (PCIe), compute express link (CXL), Aeronautical Radio, Inc. 818 (ARINC 818), Joint Electron Device Engineering Council (JEDEC) standard 204/B/C/D (JESD204B/C/D), Fibre Channel and so on, are formal descriptions of digital message formats and rules. They are separate from the physical transport layer, although some protocols […]
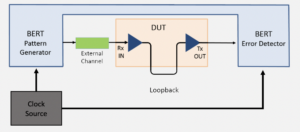
How can you minimize BERs?
Bit error ratios (BERs, sometimes called bit error rates) measure the ratio of incorrectly received bits in a data stream to the total number of bits in the stream. BERs are an unfortunate fact of life for digital and communication system designers and can be minimized and controlled, but not eliminated. BERs are related to […]
How can TinyML support sustainability on the edge?
Sustainability can be in the eye of the beholder. That’s certainly true for the question of how can TinyML (tiny machine learning) support sustainability on the edge? From a societal perspective, The United Nations Educational, Scientific and Cultural Organization (UNESCO) believes that TinyML can help to achieve its Sustainable Development Goals (SDGs). From an engineering […]