RISC-V is growing rapidly. Semico Research has projected that 62.4 billion RISC-V CPU cores will be sold in 2025. While that’s only about 6% of the overall CPU core market, RISC-V is an emerging technology that most designers should follow and become increasingly familiar with. RISC-V is becoming more commercially attractive as a result of recent developments in design and validation tools (that will be the focus of the second FAQ in this series). The emergence of RISC-V based devices optimized for specific applications such as the IoT and wearables, embedded systems, artificial intelligence (AI), machine learning (ML), virtual reality (VR), and augmented reality (AR) (to be discussed in FAQs 3 and 4).
RISC-V is software; it is an open standard instruction set architecture (ISA) based on established reduced instruction set computer (RISC) principles. Compared with proprietary ISAs such as those from Arm and Intel, RISC-V’s open-source nature brings potential benefits in terms of stability, scalability, and security. And unlike proprietary ISAs, the RISC-V ISA is provided under open source licenses that do not require fees to use.
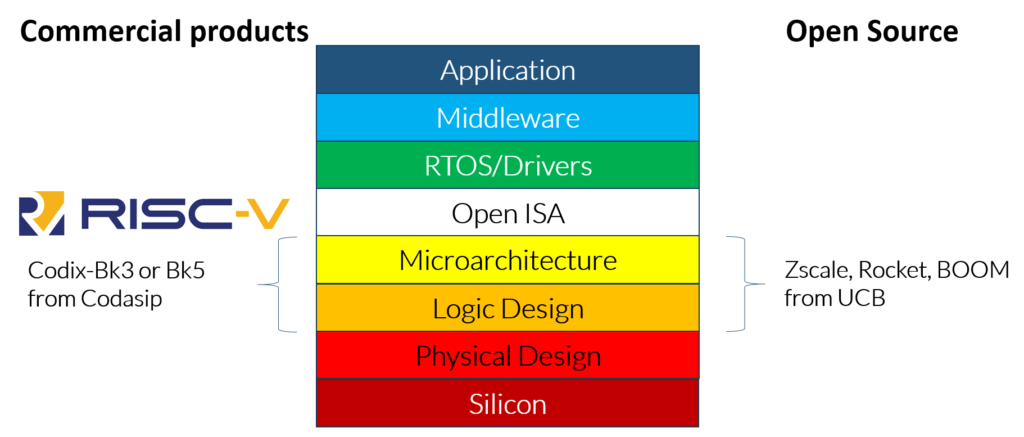
RISC-V is designed with a small, fixed-base ISA. It includes modular fixed-standard extensions that can be used with the majority of code. This architecture enables the development of application-specific extensions without needing to modify the standard ISA core. In addition to enabling customization, this approach is expected to prevent, or at least minimize, fragmentation of the RISC-V software ecosystem.
RISC-V is primarily used today in applications such as the IoT, wearables, AI/ML, and VR/AR, where it can bring substantial near-term benefits. Applications in embedded systems for RISC-V are just starting to emerge, and they often use a RISC-V core as an accelerator or other peripheral for the main core, which is usually an Arm core.
The European Innovation Action De-RISC is preparing a full hardware-software platform based on RISC-V for the space and aviation market. The use of RISC-V is expected to help to future-proof the platform, thanks to ever-increasing support for the open-source ISA, at a time when the proprietary PowerPC and SPARC architectures traditionally used in aviation and space systems are experiencing a loss of momentum. As a result, the space industry cannot leverage software from the commercial domains, driving a need to shift to architectures used in higher volume commercial markets. The final platform will be portable to other architectures, and it will also provide superior fault tolerance.
Frozen RISC-V is stable
Stability of the base instruction set and core is a key goal and benefit of RISC-V. The RISC-V base ISA and privileged architecture specifications have been ratified and are “frozen.” The RISC-V base architecture is the interface between application software and hardware. Software that’s coded to this specification is expected to continue to work on RISC-V processors in perpetuity, even as the architecture evolves through the development of new extensions.
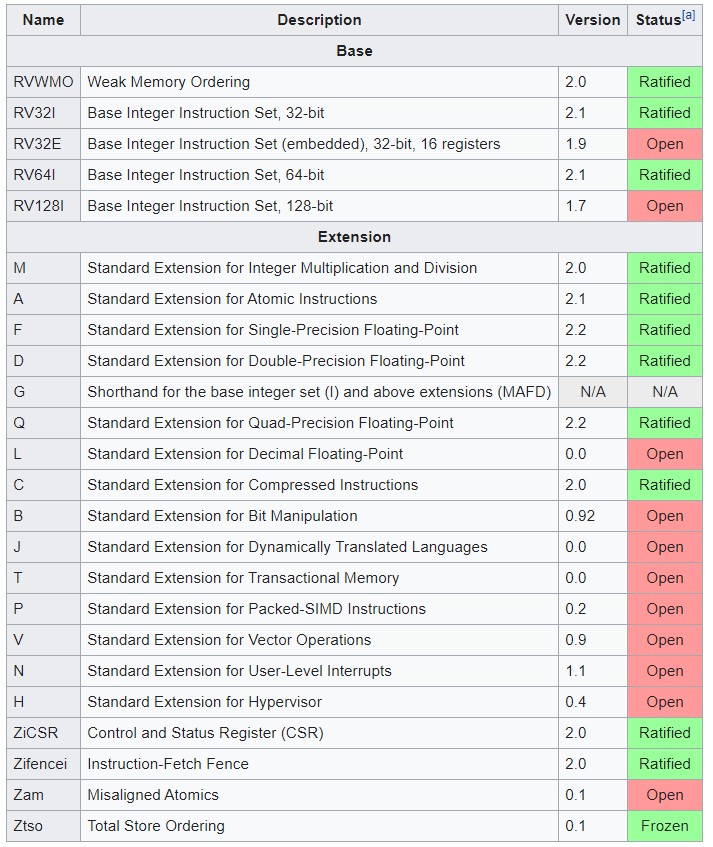
The ratification of the privileged architecture specifications will directly support the existing collaboration between the Linux Foundation and RISC-V Foundation. This cooperation is expected to result in more robust support and educational tools for the active RISC-V community and enable operating systems, hardware implementations, and development tools to scale faster. The RISC-V privileged architecture supports the use of RISC-V hardware with software such as Linux and FreeBSD. Use of these specifications is expected to increase operating system developers and hardware vendors’ confidence that their work will be compatible.

Scalability and RISC-V
The stability of frozen RISC-V means that developers can optimize code with minimal memory needs and low power consumption while maintaining scalability and compatibility for future designs. There is also the opportunity to develop extensions to the basic ISA. These extensions may impact performance in the form of varying latencies, sizes, and power consumption. Still, there will always be the underlying compatibility resulting from the inherent stability of frozen RISC-V.
Maintaining long-term stability throughout the ISA ecosystem was a priority during the development of RISC-V. And it was implemented with 32-bit, 64-bit, and (eventually) 128-bit address spaces in mind, ensuring that compatibility is maintained in the future. RISC-V was also designed from the beginning to enable extensions, supporting extensibility and the flexibility to provide for unknown future application needs, as well as the need for differentiation and optimization between applications.
The 128-bit ISA is left intentionally undefined. There is little practical knowledge about the use of 128-bit memory capacities and structures in embedded systems. However, the fact that RISC-V has a roadmap that includes a 128-bit ISA gives designers the comfort of knowing that all code developed for current iterations of RISC-V will be able to run on similar RISC cores far into the future. Using RISC-V “future-proofs” software development efforts.
Security was also baked into RISC-V from the beginning. It was not bolted on as an afterthought. As discussed in the following section, its open-source nature gives RISC-V a significant advantage in security compared with legacy proprietary ISA such as Intel and Arm.
Lower security risk is possible with RISC-V
In a recent development, GlobalPlatform and RISC-V International signed a memorandum of understanding to help accelerate the development of open standards for the hardware design of embedded components in connected devices for the Internet of Things (IoT). This includes processors embedded with Trusted Execution Environment (TEEs), which are witnessing significant growth.
GlobalPlatform is chartered to support IoT device makers and certification bodies in adopting the Security Evaluation Standard for IoT Platforms (SESIP) methodology and establishing their own IoT device security certification schemes. SESIP provides a common and optimized approach for evaluating the security of connected products that meet the specific compliance, security, privacy, and scalability challenges of the evolving IoT ecosystem.
The Security Standing Committee at RISC International brings together industry leaders to share findings, develop consensus around best security practices and identify potential security improvements for RISC-V based IoT devices, embedded systems, AI/ML, and other implementations. The Committee initially included 25 RISC-V Foundation members, including Berkeley Architecture Group, Bluespec, CSIRO’s Data61, Dover, Draper, Esperanto Technologies, Indian Institute of Technology (IIT) Madras, Intrinsic ID, Galois, Hex Five Security, Microsemi, Micron Technology, NXP, Rambus, SecureRF Corporation, SiFive, and Western Digital.
Numerous RISC-V member organizations have already introduced security solutions such as Dover Microsystems CoreGuard and SecureRF WalnutDSA. The Security Standing Committee, chaired by Rambus, has already contributed a draft specification for cryptographic extensions to the RISC-V ISA and a proposed approach to trusted execution environments for deeply embedded RISC-V devices. In addition, the ongoing collaborative work in other technical working groups on specifications for the RISC-V privileged architecture, vector extensions, and instruction set compliance demonstrates the high degree of industry interest and cooperation in security.
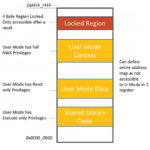
A variety of applications such as ADAS, industrial controls, and aerospace/military systems required trusted components. In many cases, the chips must be verifiably free of malicious code. In terms of this type of verification, RISC-V has advantages over Intel or Arm processors. RISC-V is open-source, enabling suppliers to reveal the complete register-transfer level (RTL) source code, supporting complete verification. When using other technologies such as Intel or Arm, commercial and/or licensing restrictions often prevent a full review of the RTL.
SiFive Shield is another example of an open, scalable platform architecture designed to enable whole SoC security for RISC-V designs. The needs of modern SoC design dictate the need for a scalable security solution, offering a trusted computing base with clear root-of-trust, and crucially, it is auditable. Customization is also key, as a single offering fitting all approaches does not align to the needs of the next generation of domain-specific processors now being designed.
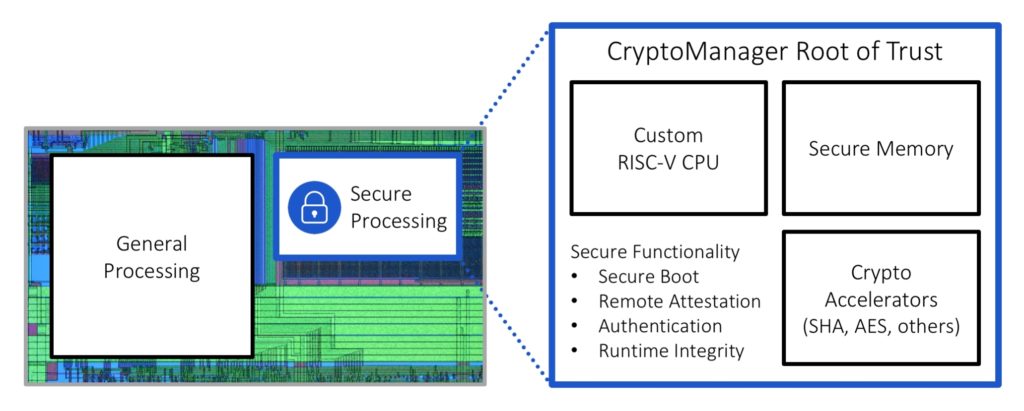
In Rambus’ CryptoManager Root of Trust, the RISC-V core is located on the same silicon as the general processor but physically separated by a secure boundary. It can run algorithms and processes within that secure boundary to protect against a wide range of attacks, including side-channel attacks, and protect against software vulnerabilities and exploits. It can also prevent device cloning.
What is the risk with RISC-V?
While RISC-V has made great strides in development and initial adoption, it’s still early days for the technology. As a result, there are unknowns and some level of risk.
A key challenge to more wide-spread adoption of RISC-V is the lack of a well-developed software ecosystem. That is one of the reasons for RISC-V’s early-term adoption in the IoT and AI/ML spaces; both of those technologies are themselves emerging and need the performance benefits delivered by RISC-V.
Compared with other ISAs, such as those from Arm and Intel, RISC-V has a very short history and is relatively immature. One result of this fact is a lack of performance benchmarks for comparing RISC-V with other platforms or for comparing various RISC-V implementations. And once the needed benchmarks are developed, there is some concern that RISC-V may have lower performance than the much more mature and well-understood alternatives.
And there’s a lack of testing standards and tools compared with mature ISAs such as Intel and Arm. This is one area that is beginning to see accelerating developments and progress. The growing availability of tools reducing the risk of using RISC-V is the focus of the next FAQ in this series.
References
Dependable Real-time Infrastructure for Safety-critical Computers, EU De-Risc
Does RISC-V mean open source processors?, Codasip
RISC-V, Wikipedia
RISC-V International
RISC-V International and GlobalPlatform Partner to Enhance Security Design of IoT Devices, GlobalPlatform
RISC-V Cores’ CAGR to Approach 160% by 2025, says Semico Research, Semico Research



Leave a Reply